The Use of Proxies in Process Mining: 2025 Guide
If you want to enhance your process analysis, you’re in the right place. Enter process mining. It isn’t just another buzzword. It’s a transformative technique endorsed by top experts. Think of it as your X-ray vision into the heart of your organization’s IT systems. With this tool in hand, you’re not just skimming the surface. You’re diving deep, extracting event logs, and decoding patterns.
But here’s the kicker: diving deep into data territory requires serious armor. And that’s where our proxies step into the spotlight. They ensure efficient data extraction with top-tier security. Let’s pull back the curtain on melding proxies with the mining tool in this guide full of tips, watch-outs, and the next-gen strategies setting the industry abuzz.
What Is Process Mining?
It’s the bridge between data science and business process management. It’s the science of analyzing event logs from IT systems to understand the actual processes.
However, it isn’t just about collecting information; it’s about making sense of it. Every time users interact with a system, whether placing an order, updating a record, or even just logging in, they leave behind a trail. This trail, often stored in event logs, is pure gold for anyone looking to understand how processes operate beyond what’s on paper.
But here’s where it gets even more fascinating. The mining tools don’t just provide a static snapshot; they offer dynamic visualizations. You can see the flow of processes, identify where delays occur, and pinpoint areas that deviate from the intended process.
You might ask, “What makes this revolutionary?” Well, traditional methods of understanding processes often relied on workshops, interviews, and manual observations. While these methods have merits, they’re time-consuming and prone to biases or inaccuracies. Process mining, on the other hand, provides an objective, data-driven perspective. It cuts through assumptions and gets to the heart of processes’ functions.
Types of Process Mining
Indeed, it isn’t one-sided. One can commonly categorize it into the following types:
- Discovery: This is the exploratory phase where the primary goal is to discover the actual processes taking place within an organization by analyzing event logs. It’s like piecing together a puzzle, revealing the complete picture of how operations unfold.
- Conformance: Think of this as the auditing phase. Here, the processes discovered are compared against the ideal or intended processes. It helps identify deviations and ensure that operations align with the set standards.
- Enhancement: This is the optimization phase. Processes are enhanced and refined based on the insights from discovery and conformance. It’s about taking what’s good and making it even better.
The Middleman Between Data Mining and BPM
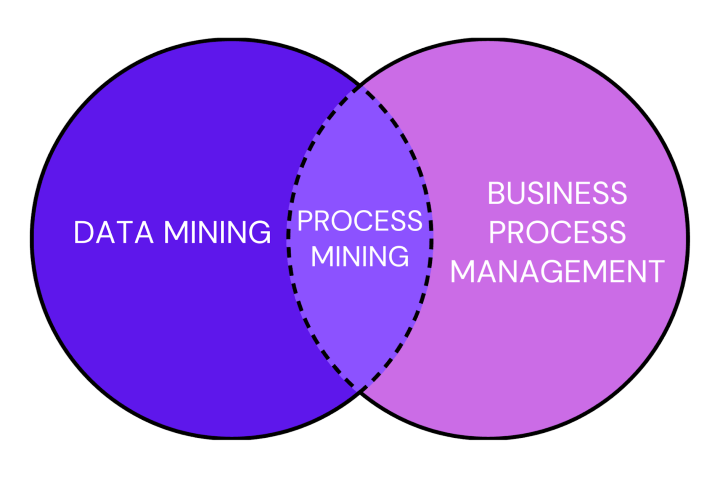
Understanding technology nuances is vital in business analytics. Let’s delve deeper into these concepts.
Comparison with Data Mining
Both tools are about exploring data. However, their focus and applications differ significantly. The mining tool is all about unraveling the sequence and flow of events within processes. It seeks to understand the intricacies of how operations unfold. On the flip side, data mining casts a broader net. It’s not just about sequences but about spotting patterns, correlations, and overarching trends in vast data pools. While the former technique zeroes in on visualizing, monitoring, and refining processes, data mining is the detective that extracts nuggets of valuable insights.
Comparison with Business Process Management (BPM)
When we shift our gaze to BPM, the distinction becomes analysis versus action. Process mining is the diagnostician’s keen understanding and analysis of the actual processes at play within an organization. It’s about getting to the heart of how things work. In contrast, BPM is the strategist and executor. It’s a comprehensive approach encompassing the design, modeling, execution, monitoring, and fine-tuning of business processes.
Use Cases
This tool offers a magnified view of processes, revealing their strengths and areas ripe for enhancement. Let’s explore some compelling use cases where it has proven its mettle.
- Supply Chain Optimization: The technique can identify delays and inefficiencies in supply chain operations. By visualizing the flow of goods, information, and finances, businesses can streamline their supply chain, ensuring timely deliveries and optimal resource utilization.
- Customer Journey Mapping: Understanding the customer’s journey is paramount for modern businesses. The mining tool deciphers the touchpoints, interactions, and pathways customers traverse, offering insights to enhance their experience and boost satisfaction.
- Compliance and Auditing: It aids organizations in ensuring that operations align with regulatory standards. By highlighting deviations and non-compliant activities, it acts as a shield against potential legal repercussions.
- Healthcare Workflow Analysis: The tool dissects patient pathways, treatment protocols, and administrative workflows. One can use this information to enhance patient outcomes and streamline healthcare delivery.
- Financial Transaction Analysis: The process offers a lens to view financial processes, ensuring accuracy, reducing fraud risks, and optimizing transaction workflows.
5 Questions & Answers
To help you better understand the topic, let’s answer some of the most common questions.
1. How Does Mining Work with Information Systems?
Every action in your IT system tells part of your operations’ story. The tools in question read these chapters, extracting event logs and using algorithms to reconstruct and visualize the narrative. But it’s not just about recounting the tale; it’s about understanding its nuances. By applying data science techniques, this technology can identify patterns, bottlenecks, and areas of improvement, offering a clear and objective perspective on operational efficiency.
2. How Can This Tool Improve Efficiency and Quality?
It acts as a diagnostic tool for your business. Visualizing the actual flow of processes identifies inefficiencies, deviations, and bottlenecks. This clarity allows businesses to streamline operations, optimize resources, and align processes with ideal models, enhancing quality and customer satisfaction.
3. How Is Process Mining Different from Traditional Process Discovery?
Traditional process discovery often relies on manual methods like interviews, workshops, and observations. While these methods provide insights, they can be subjective and time-consuming. In contrast, mining technology offers an objective, data-driven approach. Analyzing event logs provides a real-time, accurate representation of processes, eliminating biases, and assumptions.
4. Is It Possible to Integrate This Tool with Other Business Intelligence Tools?
Absolutely! You can integrate it with other BI tools to comprehensively view business operations. By combining the insights from mining with data analytics, predictive modeling, and other BI tools, businesses can gain a holistic understanding of their operations, driving informed decision-making.
One of the significant advantages of integrating it with BI tools is the ability to visualize and analyze process data alongside other business metrics. This combined view can offer deeper insights into how processes impact overall business performance sources.
Popular BI tools to integrate with include:
- Microsoft Power BI: A widely used BI tool for advanced information visualization and analytics. Integrating mining features within PowerBI puts process understanding right within the BI consoles, which many companies already utilize.
- Qlik: Another powerful BI tool that can be combined to offer dynamic visualizations and deep insights into business processes.
- Tableau: Known for its interactive visualization capabilities, One can integrate Tableau to provide a combined view of process and business information.
Moreover, combining the mining tools with AI and predictive analytics can further enhance the insights derived, allowing businesses to forecast potential bottlenecks before they occur.
5. How Does Mining Support Digital Transformation Initiatives?
Digital transformation is about leveraging technology to enhance business operations. In this context, this tool provides insights into current processes, highlighting areas for improvement. With these insights, businesses can implement technology solutions that align with their objectives, ensuring that their digital transformation initiatives are grounded in data-driven decisions.
Why Use Proxies?
Process mining revolutionizes business operations optimization. But here’s a twist: while it is powerful, combining it with proxies can supercharge its capabilities. You might be wondering, “Why bring proxies into the mix?” Let’s break it down for you.
Main Benefits of Using Proxy Services
Here are the core benefits of integrating proxies into your business endeavors.
- Enhanced Data Accuracy: Proxies ensure that your mining data is accurate. By routing requests through different IP addresses, proxy services can bypass geo-restrictions and access information from various regions, providing a comprehensive dataset.
- Scalability: With proxy services, you can send multiple requests simultaneously without being flagged or blocked. It means you can mine data at a larger scale faster.
- Avoiding Rate Limits: Websites often have request limits to prevent overload. Proxies can help bypass these rate limits by distributing requests across multiple IP addresses.
- Data Redundancy Prevention: Proxy services can help in avoiding redundant data collection. They ensure the same information isn’t mined multiple times by rotating IP addresses.
- Enhanced Performance: Proxies can cache data, which means repeated requests for the same information can be fetched faster, improving the overall performance of the mining process.
- Geo-specific Insights: Understanding processes across different regions is crucial for those businesses that operate globally. Proxies allow for geo-specific mining, providing regionally relevant insights.
Best Proxy Types
Not all proxies suit equally well for business purposes. Here are some of the best types to choose from.
| Proxy Type | Description | Benefits | Disadvantages |
| Datacenter IPs | IPs of servers located in data centers. | – Fast and reliable.- Ideal for large-scale data mining tasks. | – Can be detected and blocked if used aggressively.- Not as genuine as residential IPs. |
| Residential Proxies | Real IP addresses provided by ISPs. | – Authentic and harder to detect.- Less likely to be blocked. | – Slower than datacenter IPs due to being genuine.- Can be more expensive. |
| SSL Proxies | Proxies that encrypt data between the client and the server. | – Enhanced security.- Protects mined information from potential threats. | – Can be slower due to the encryption process.- Might not be supported by all websites. |
| SOCKS Proxies | Can handle any type of traffic, unlike HTTP proxies. | – Versatile for various data mining tasks.- Suitable for diverse traffic types. | – More complex setup compared to other proxies. |
A Guide for Using Proxies
Integrating proxies can boost mining efficiency and effectiveness. But they can multiply their power if utilized correctly. Here’s a complete step-by-step guide to unveil a real proxy power.
1. The Art of Proxy Rotation
Consistent rotation of proxies is crucial. It ensures you steer clear of rate limits and minimizes the risk of your proxies getting blocked. Thus, employ rotating proxies instead of static types. You can configure them to switch after a specific number of requests or after predetermined time intervals.
By the way, if you want to learn about the additional benefits of proxies, read this article about the best rotating proxies.
2. Geographical Precision in Data Collection
If you’re a business with a global footprint, consider proxies for accessing from different parts of the world, thus ensuring data collection is relevant to specific regions. Maintaining a diverse set of proxies from various geographical locations and deploying them based on the regional relevance of the mining task is the best way out.
3. Upholding Data Integrity
While proxies facilitate access to a broader data spectrum, maintaining the integrity of the mined information is paramount. Thus, its regular validation is essential. Additionally, cross-referencing with alternate sources can further ensure information accuracy.
4. Speed Optimization
In any business tool, time is a critical factor. Slow proxies can turn into bottlenecks, impeding the efficiency of operations. It’s essential to periodically assess the speed of your proxies, phasing out the slower ones and integrating faster alternatives.
5. Fortifying Security
Though proxies inherently enhance security, you must ensure end-to-end encryption, especially when you handle sensitive information. SSL proxies, which encrypt information between the client and the proxy server, offer an added layer of protection.
6. Navigating the Legal Landscape
While proxies offer expansive data access, adhering to the terms of service of the websites being mined is essential. When in ambiguity, seeking legal counsel can provide clarity. Please, address the article about proxy compliance and legal considerations if you need further clarification.
7. Staying Agile: Monitoring and Adaptation
The digital domain is dynamic. Strategies that are effective today might become obsolete tomorrow. Periodically reassess your proxy strategy, making adjustments based on emerging trends and challenges in process mining.
8. The Premium Proxy Advantage
While the allure of free proxies is undeniable, they often lack reliability and speed. Thus, your best decision is to invest in premium proxies for enhanced speed, reliability, and security.
9. Team Empowerment
The efficacy of proxies is contingent on the team’s proficiency in wielding them. Regular training sessions can ensure that the team is well-versed in the best practices of proxy usage.
Dreaded Mistakes When Using Proxies
Like any powerful tool, proxies can lead to significant pitfalls if not used correctly. Organizations often make three crucial mistakes when utilizing them.
Overlooking Data Validation and Verification
One of the most common pitfalls is jumping to conclusions or making recommendations without proper validation and verification of the mined data. Implementing changes based on this information can lead to wasted resources, misaligned strategies, and even further process inefficiencies.
The Solution: Always cross-check the mined data with other reliable sources. Use statistical methods to validate its accuracy and consistency. Moreover, ensure that the proxies used are reliable and provide accurate information.
Neglecting Data Quality and Completeness
Poor information quality in event logs, problems with timestamps, event granularity, ambiguity of activity names, and missing data segments can severely impact mining results. Incomplete or poor-quality information leads to a skewed understanding of processes, which results in wrong insights and recommendations.
The Solution: Regularly audit and clean the event logs. Ensure that the information sources are reliable and that the proxies are fetching complete and unaltered information. Address any gaps in data collection and ensure that all relevant events are logged.
Misusing Proxies and Facing Legal Repercussions
While proxies can help access a wealth of information, there’s a thin line between ethical data mining and breaching terms of service or even legal boundaries. Overaggressive data mining using proxies can lead to IP bans, legal actions, and damage to the company’s reputation.
The Solution: Always respect the terms of service of websites from which you’re mining data. Ensure that the use of proxies aligns with legal and ethical standards. If in doubt, always consult with legal counsel to ensure compliance.
Future Trends for 2025
This tool continues to evolve, adapting to the changing landscape of business needs and technological advancements. In 2025, several trends will shape this process, reflecting the industry’s commitment to innovation and efficiency.
Integration and Automation
A significant trend in process mining is its growing integration with other platforms. Notable tech giants have begun acquiring this solution, which led to a surge in integrations. For instance, IBM’s acquisition of MyInvenio and SAP’s merger with Signavio indicate this trend. Moreover, there’s a growing emphasis on using mining as an enabler for automation. It is paving the way for more effective and targeted robotic process automation (RPA) initiatives by providing a clear understanding of underlying business processes.
Customer-Centric Mining
While traditionally mining has been inward-focused, emphasizing internal process optimization, there’s a growing shift towards external, customer-centric process mining. This approach involves analyzing processes that interact directly with customers or partners. Integrating capabilities from customer service platforms and leveraging customer feedback allows businesses to align their internal processes better with customer needs, leading to enhanced customer experiences.
Enhanced Collaboration through Cloud-Based Platforms
As businesses increasingly adopt cloud solutions, the mining tool also makes its mark in the cloud ecosystem. Cloud-based mining platforms offer scalability, flexibility, and real-time collaboration. They allow teams from different locations to work together seamlessly, analyzing processes and sharing real-time insights. It speeds up the decision-making process and ensures that insights and recommendations are consistent across the organization. Additionally, cloud platforms can integrate with other cloud-based tools, creating a unified ecosystem for data analysis, storage, and process optimization.
Predictive and Actionable Insights
Process mining gradually moves from a descriptive to a predictive mode. Instead of merely outlining what happened, modern tools forecast what could happen next. This shift is particularly evident in developing causal mining techniques that establish transparent causal relationships between problems and potential solutions.
To Sum Up…
Integrating process mining with proxies offers a robust framework for data-driven decision-making and operational optimization. As we’ve explored, the synergy between these tools provides unparalleled insights into business processes, ensuring accuracy, scalability, and security. With the rapid advancements in technology and the evolving landscape of business analytics, it’s imperative to stay updated and leverage these tools effectively. Ensure your strategies are grounded in data integrity, legal compliance, and technical proficiency. Prepare to harness the full potential of this technique, and let it be the cornerstone of your business’s analytical endeavors.
