Enhancing Remote Employee Security: The Role of Static Proxies in Ensuring Secure Connections

In today’s rapidly evolving digital landscape, the shift towards remote work has become more than just a trend — it grew into a significant transformation, reshaping how businesses operate. Driven by global events and the quest for flexibility, traditional office boundaries have expanded to include home offices, local cafes, and even distant locales. However, with this expansion comes a heightened risk: the ever-present cyber threats that seek to exploit vulnerabilities in our digital connections.
Having navigated the intricacies of cybersecurity for over a decade, I can attest to the importance of building strong defenses and strategically optimizing the pathways we use. It is where the role of static proxies becomes paramount. These digital gatekeepers ensure our online interactions, especially in remote work, are secure and efficient. As we delve deeper into this topic, we’ll explore the nuances of these proxies and their pivotal role in fortifying the security of our digital communications in the age of remote work.
Understanding Proxies: A Quick Refresher
In cybersecurity, the term “proxy” often emerges as a beacon of hope for those seeking protection. But what exactly is a proxy, and why has it become such a crucial tool in our digital toolkit? Let’s embark on a brief journey to demystify this concept.
What is a Proxy?
At its core, a proxy is an intermediary between a user’s device and the internet. Imagine you’re sending a letter, but instead of delivering it directly, you hand it to a trusted friend who delivers it on your behalf. This friend acts as a “proxy,” ensuring your letter reaches its destination while keeping your identity concealed. In the digital world, a proxy operates similarly, handling data requests and responses to maintain user anonymity and enhance security.
Static (Dedicated) vs. Dynamic (Rotating) Proxies
Now, not all proxies are created equal. There are primarily two types to consider:
- Static (Dedicated) Proxies: These are like your permanent address. They provide a consistent IP address, ensuring stability and reliability. I’ve tested numerous of these services and found them particularly useful for tasks that require a consistent identity, such as accessing geo-restricted content or maintaining long-term online sessions.
- Dynamic (Rotating) Proxies: Think of these as temporary accommodations. They offer a changing IP address whenever you connect or at regular intervals. This dynamism can benefit tasks like web scraping, where avoiding detection is paramount.
The Business Case for Proxies
In the context of working remotely, proxies aren’t just a luxury; they’re a necessity. Here’s why:
- Enhanced Security: Proxies add an extra layer of defense against cyber threats, shielding employee devices and company data.
- Access Control: Businesses can use proxies to grant remote employees access to geo-restricted company resources, ensuring seamless operations regardless of location.
- Monitoring and Management: Proxies allow businesses to monitor online activities, ensuring compliance with company policies and identifying potential security breaches.
In my years of experience, I’ve observed that as businesses grow and adapt to the remote work model, the strategic implementation of proxies becomes increasingly vital. They not only bolster security but also optimize the overall online experience for remote employees.
The Advantages of Static Proxies for Remote Work
Ensuring a seamless and secure online experience is paramount in the ever-evolving world of working remotely. While businesses can employ various tools and strategies, static proxies have become a cornerstone for many. But why? It’s time to clarify.
Stability: The Bedrock of Remote Operations
One of the most significant benefits of this proxy type is its stability. Unlike their dynamic counterparts, which frequently change IP addresses, these proxies provide a consistent IP. This consistency translates to less downtime and fewer disruptions.
Imagine being in the midst of a crucial virtual meeting or accessing a vital company database, only to be disconnected due to an IP change. It’s not just an inconvenience; it can be a significant productivity drain. Over the years, I’ve tested and observed that static proxies offer a level of reliability that’s hard to match, making them an ideal choice for businesses that prioritize uninterrupted operations.
Speed: The Need for Digital Swiftness
In the digital realm, speed is of the essence. With their dedicated resources, static proxies are likely to outpace dynamic proxies. They can provide faster connection speeds since they’re not constantly rotating and are tailored for long-term use.
From uploading large files to streaming high-quality video conferences, the enhanced speed of static proxies ensures that remote employees can perform their tasks efficiently. In my experience, the difference in speed can sometimes decide between meeting a deadline and falling behind.
Security: Fortifying the Digital Frontiers
While all proxies offer security, static proxies have a unique advantage. Some websites and online services are wary of rotating IPs due to their association with web scraping or malicious activities. With its unwavering IP, a static proxy is less likely to raise red flags.
Moreover, businesses can exert better control over traffic with these proxies. Monitoring becomes more straightforward by having a dedicated IP for specific tasks or employees, and potential threats can be identified and mitigated more efficiently.
Geolocation: Navigating the Digital Borders
In today’s globalized business environment, accessing geo-restricted content is not uncommon. Whether it’s a regional database, a local intranet, or specific online services available only in certain areas, geolocation can pose challenges for remote employees.
Static proxies shine in this aspect. By providing a consistent location, these services allow remote workers to access geo-restricted company resources without a hitch. For instance, an employee in Asia can access a US-based database by using a US static proxy, ensuring they have the same access privileges as someone physically present in the US.
Common Mistakes When Implementing Proxies for Remote Work
The digital age, with all its conveniences, also brings forth a myriad of challenges, especially in cybersecurity. While static proxy services offer a robust solution to many of these challenges, their effectiveness can be compromised if not implemented correctly. Let’s shed light on some common pitfalls and how to sidestep them.
The Oversight of Education
Having a top-tier static proxy in place is one thing, but it’s an entirely different ballgame to ensure every employee understands its importance. I’ve encountered scenarios where employees, unaware of the significance, bypass the proxy, thinking it’s just another “tech hurdle.” This oversight can expose the entire network to potential threats.
✓ Expert Insight: Regularly conduct training sessions emphasizing the importance of always using the proxy. Use real-world examples to highlight potential risks and the proxy’s protective layer.
The Allure of Free Proxies
Ah, the temptation of freebies! While free proxies might seem cost-effective, they often come with hidden costs. These proxies can be unreliable, slow, and, in some unfortunate cases, even malicious. Remember, if you’re not paying for a product, someone might use you as a product.
✓ Expert Insight: Always opt for reputable proxy providers, even if it means investing a bit more. The security and efficiency they offer far outweigh the initial costs. Make sure to take note of these three points before making your final choice:
- Research: Begin with a thorough market analysis. Look for providers specializing in business solutions, as their infrastructure is often better suited for corporate needs.
- Testimonials & Reviews: Seek out feedback from other businesses. Platforms like Trustpilot or G2 can offer unbiased reviews.
- Trial Period: Before committing, opt for a trial. Hands-on testing reveals more about a service than any review.
Neglecting Encryption
While static proxy services are excellent for anonymity and access control, they do not replace encryption. Some businesses make the grave mistake of thinking that this technology is the be-all-end-all solution. Without encryption, data transmitted can still be intercepted and read by malicious entities.
✓ Expert Insight: If your team uses VPNs with proxies, ensure the VPN employs robust encryption standards. Remember, a chain is only as strong as its weakest link.
Lax Maintenance and Updates
The digital landscape is ever-evolving, and what’s secure today might be vulnerable tomorrow. Relying on an outdated proxy setup is akin to leaving your backdoor unlocked in a neighborhood known for burglaries.
✓ Expert Insight: Schedule regular maintenance checks and updates for your proxy setup. Stay informed about the latest developments in the proxy world and adjust your strategies accordingly.
Diversifying the Digital Arsenal: Other Essential Tools for Remote Worker Security
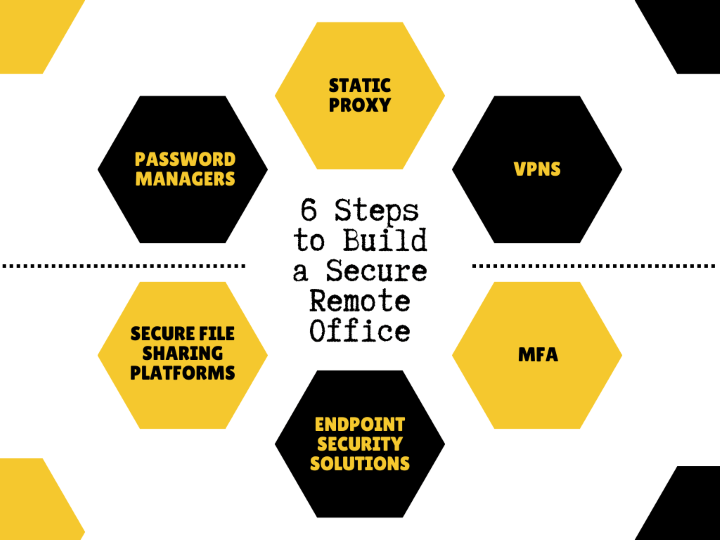
In cybersecurity, while static proxies stand out as a formidable line of defense for remote workers, they are but one piece of the intricate puzzle. As remote work continues to burgeon, the need for a multi-faceted approach to security becomes paramount. In this section, I will explore other essential tools remote workers can employ to fortify their digital defenses.
Virtual Private Networks (VPNs): The Digital Cloak
VPNs have long been the go-to solution for individuals and businesses seeking an added layer of privacy and security. By creating an encrypted tunnel between the user’s device and the internet, VPNs ensure that all data transmitted remains confidential and impervious to prying eyes. For remote workers accessing sensitive company data, a VPN is indispensable.
- Actionable Tip: Opt for VPNs that offer strong encryption standards, have a no-logs policy, and provide servers in multiple locations for optimal performance.
Multi-Factor Authentication (MFA): Double the Defense
MFA adds a layer of security by requiring users to provide two or more verification factors to access a resource. It could be something they know (password), something they have (a smartphone or hardware token), or something they are (fingerprint or facial recognition). By employing MFA, even if a cybercriminal manages to steal a password, they would still be barred from accessing the account without the second verification factor.
- Actionable Tip: Implement MFA across all company accounts, especially those containing sensitive data. Encourage employees to use authentication apps or hardware tokens as they offer better security than SMS-based verification.
Endpoint Security Solutions: Guarding the Entry Points
Endpoint security tools protect the endpoints or entry points of end-user devices like computers and mobile devices from being exploited by malicious actors. These solutions detect, block, and remediate threats, ensuring that even if an employee accidentally clicks on a malicious link, the danger is neutralized before it can cause harm.
- Actionable Tip: Choose comprehensive endpoint security solutions that offer real-time threat detection, automatic updates, and integrate seamlessly with other security tools.
Secure File Sharing Platforms: Safe Data Transfers
Remote work often involves sharing files and documents. Standard email or cloud storage might offer a lower level of security needed for confidential company data. Secure file-sharing platforms encrypt files during transit and at rest, ensuring that only the intended recipient can access them.
- Actionable Tip: Opt for platforms that offer end-to-end encryption, password protection, and expiration dates for shared links.
Password Managers: The Digital Vault
Remembering complex passwords for multiple accounts can be daunting. However, using the same password across platforms is a security risk. Password managers solve this dilemma by securely storing all passwords in an encrypted vault. With a master password, users can access all their credentials, ensuring they maintain strong, unique passwords for every account.
- Actionable Tip: Encourage employees to use password managers and regularly update their master password. Some managers also offer breach alerts, notifying users if one of their accounts is compromised.
The Future of Remote Work and Cybersecurity
The digital transformation of the workplace, accelerated by unforeseen global events, has firmly established working remotely as a significant component of the modern work paradigm. As we look ahead, several data points and studies provide insights into the trajectory of remote work and its implications for cybersecurity.
According to a report by Upwork, by 2025, an estimated 32.6 million Americans are projected to be working remotely, accounting for about 22% of the workforce. This projection underscores remote work’s growing acceptance and integration into mainstream business operations. Similarly, a Gallup survey from June 2022 revealed that 8 out of 10 people work in hybrid or remote setups, with only 2 in 10 being on-site.
With this shift, the role of static proxy services in the cybersecurity landscape is bound to evolve. The demand for secure, stable, and efficient online connections will surge as the remote job becomes more prevalent. With their inherent advantages, these proxies will be central to meeting these demands.
However, businesses must remain vigilant. The cybersecurity landscape is dynamic, and as remote work practices evolve, so will the threats targeting them. Staying informed, adopting best practices, and being proactive in cybersecurity measures will be more crucial than ever.
Conclusion
In the digital age, where working remotely is becoming the norm rather than the exception, the significance of static proxies in bolstering remote employee security cannot be overstated. These proxies serve as the silent sentinels, ensuring stable, swift, and secure connections, thereby fortifying the digital fortresses of businesses.
As we move forward, it’s imperative for companies to not only recognize but also prioritize the pivotal role of cybersecurity. The digital realm is vast and filled with both opportunities and threats. I urge businesses to take proactive steps, make informed decisions, and champion cybersecurity as a cornerstone of their remote work strategy.
