How Do I Create A Proxy?
Don’t let the browsing restrictions keep you from doing what you want. You can take back control by setting up your proxy server in a few simple steps. No more lists of “banned sites” and restricted access to your favorite websites.
When traditional means fail, it’s time to take matters into your own hands. Setting up your server is quick and easy, and saves you the hassle of being constrained by network restrictions.
Proxies are often used by companies to keep user data secret or to function as firewalls for added protection. So take control of your browsing by setting up your proxy in a matter of minutes.
What Is A proxy?

A proxy server acts as an intermediary between your device and the Internet. When you transmit traffic through the server, it appears to come from the server’s IP address and not from your computer. Your browser communicates with the server, which connects your browser to the Internet using HTTP or SOCKS protocols.
These proxies build a bridge between the website you visit and your device. Your Internet traffic is routed through a remote machine that helps you connect to the host server.
How Do Proxies Work?
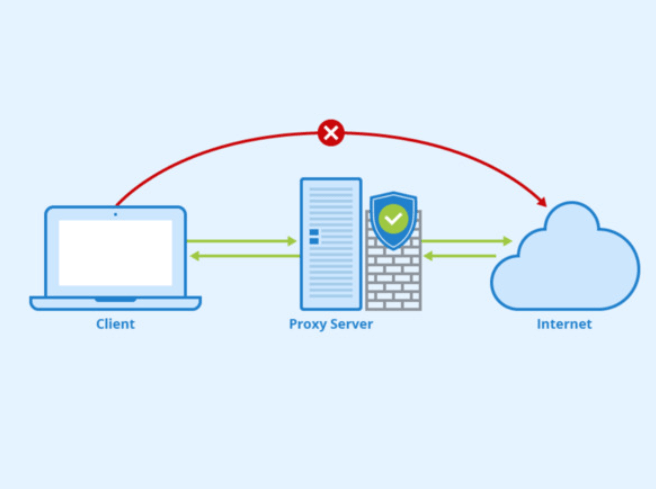
Proxies establish a connection between your computer and the Internet so that you can access websites and pages with geographical restrictions through your browser. The connections are not encrypted, so your personal data and online activities are unprotected from potential threats. It only protects your privacy by hiding your identity from the website or web application you are using, but it does not protect sensitive data. The HTTP proxy can help you access blocked websites, but it does not provide complete security for your online activities.
The Pros and Cons of Proxies
Pros of using proxies
Here are some advantages of having such tools:
- It helps you remain incognito on the Web by hiding your IP.
- Proxy server free usage is available for everyone, you don’t have to pay to use them.
- You can set up your server to restrict access to certain websites, which is useful for companies to monitor their employees’ Internet usage.
- It can help protect your computer from malicious websites by blocking access to them.
- By bypassing geographical restrictions, the servers can help you access blocked Internet sources.
Cons of using proxies
The disadvantages are related to the following points:
- Your Internet traffic is not private, and the owner of the server can disclose it.
- Proxies are usually set up to work with specific programs or browsers, not the entire network.
- The server does not encrypt your traffic or information, which makes you more vulnerable to attacks.
- The speed of the connection may slow down if many people use the same server.
Types of Proxies
Public proxies
These servers can accept multiple connections from different users simultaneously. Many public proxies have emerged that allow unauthorized users to connect to them. However, these servers are often unstable and offer very different speeds. Moreover, you have to trust the operators of these anonymous servers with your confidential data.
Private proxies
Such servers are not publicly accessible and usually charge a fee. For instance, offers both HTTP and SOCKS5 services, and BTGuard and TorGuard offer SOCKS5 services for “torrents”.
Private proxies are much more trustworthy and are operated by reputable organizations that offer comprehensive support. They also offer specialized software.
SOCKS
SOCKS are not limited to web proxy traffic, but still, only work at the application level. You can install them on a streaming video application, a peer-to-peer platform, or a gaming application. SOCKS does not interpret network traffic, which makes them much more adaptable. However, since they handle more web page proxy traffic, they tend to be a bit slower.
HTTP
HTTP is designed to process web pages. If you configure your browser with HTTP, all your traffic will be HTTP. It is useful for browsing the Internet and also allows you to visit geographically restricted websites.
Because the HTTP protocol interprets traffic only at the HTTP level, it can only handle the traffic that begins with HTTPS:// or HTTP://, which means it’s only useful for browsing the Internet. However, since it only processes HTTP requests, it is faster than VPN or proxy socks.
How Do I Create a Proxy?
First of all, let’s consider the prerequisites. You’ll need a hosting service that meets some requirements, PHP7 or higher, and cURL. If you have paid to host, the availability of these features is almost guaranteed. If you use a free proxy server, cURL may be disabled. You can check this on your host’s website. Indeed, you need your hoster’s permission to set up a proxy server.
1. Download and Install PHP
Once you’ve met those conditions, it’s time to upload and set up PHP-Proxy. This free, stand-alone PHP script is lightweight and incredibly easy to set up.
Download the files from the site to a subdirectory on your web server and create a subdirectory in the “www” directory or domain name (e.g., domain.com). Do not use the word “proxy”; use “surf” or”web” instead to avoid detection by some companies.
You have several options for downloading the files listed below from the easiest to the most time-consuming.
Extract ZIP archive: Check if your file manager has an “extract”, “unzip” or “unpack” button, which depends on your host. If you have trouble finding it, ask your web hosting service for help. Unpack the files into a public directory.
FTP access: Use an FTP program to access your host and let it move files around while you take a break. Most hosting companies support this feature.
Manual Upload: This is a last resort. If the two described options are not available, you’ll either have to manually upload all the files and folders or find a new hoster. The latter option may not be a bad idea.
2. Edit the “config.php” file
To complete the installation, open the “config.php” file and add a random value between quotes to the line $config[‘app_key’]= ‘ ‘. After these actions, save the file and your server is now ready to use.
To access PHP, open the web browser and change to the directory where you downloaded the files. This will load the PHP page and you can then enter any URL address in the search box and surf the web safely.
When PHP is running, you can use it as you wish. This service hides your IP address, allowing you to access anonymous proxy servers for surfing the Internet.
3. Install SSL Encryption
Although you can use PHP right away, it is not recommended to use it without taking one more step. If you want to ensure the security of your network, it is very important to set up SSL encryption. Fortunately, this is also a quick and easy process.
You should install Certbot. It is a free automated certificate tool. Once you visit the Certbot website, it will provide a detailed installation guide depending on your server and operating system.
Replace “YourDomainName.com” with your domain name in the command script during the installation process. When Certbot asks you if you want to redirect all traffic to HTTPS, select “Yes” as this is the safest choice. Your PHP will then be ready for secure use.
How to Set up a Proxy Server Under Windows?
Windows 10 instructions

If you are using the Windows 10 operating system on your computer, the setup process is easier. Follow these simple steps to install the server with the built-in Windows 10 prerequisites.
First, open the settings and select the “Network and Internet” option. Then, select the “Proxy” section and make sure that the “Automatically detect settings” option is enabled. Then enable the “Set up script” option and enter the address of the proxy server you want to run. After you click “Save”, Windows will redirect your web traffic through the server.
If Windows could not detect the server, you can configure it manually. In the settings, enable the “Use a proxy server” option under “Manual setup”. Instead of the script address, you need to enter the IP address of your server, which you get from your ISP. Once you have entered the required data, select “Save” and that’s it.
Now you can use the Internet as you see fit. You can save bandwidth and visit forbidden websites.
If you prefer to leave the installation process to someone else, you can also use one of the popular proxies.
Windows 11 instructions

The Windows 11 operating system, like Windows 10, has proxy settings.
To get started, press the Windows key and type “change proxy settings” in the search bar. Click on the first option that appears, and you’ll be taken to the built-in settings.
To use the proxy script, check the “Automatically detect settings” option and then click “Setup” next to “Use setup script”. Check the “Use proxy server setup script” option and enter the address of the script in the field. Then save the operation.
If you prefer to configure the settings manually, click “Setup” under “Manual proxy setup” in the settings window. Check the “Use proxy server” option and enter the port number and IP of your server. After you have filled in all the required fields, select “Save” to complete the settings.
Proxies Vs. VPNs: What’s The Difference?
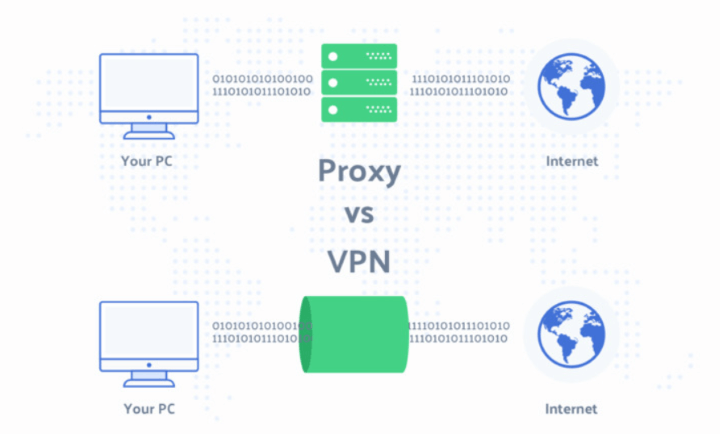
There is also another method to access prohibited content. A virtual private network (VPN) is a tool that allows users to connect to a secure private network over the Internet.
A VPN client establishes a secure and encrypted connection between your device and a VPN server, through which you can access websites and data without revealing your IP address or personal information. VPN software hides your online identity from the websites and applications you use and hides your online activity from your ISP. Redirecting your traffic through a VPN ensures that your data is safe, making it an ideal solution for online shopping, banking, or sending official emails over public WiFi networks. VPN services also prevent hackers and other malicious actors from spying on your traffic and compromising your sensitive data.
There are six main types of VPN servers:
- OpenVPN: It is an open-source server that offers a wide range of encryption features.
- L2TP: Layer 2 Tunnel Protocol is a highly secure VPN, but it is slower than OpenVPN.
- PPTP: Point-to-Point Tunneling Protocol is a fast and easy-to-configure tool, but it is very insecure and should be avoided.
- IKEv2: Internet Key Exchange Version 2 is a secure VPN that is faster than PPTP and L2TP. It supports AES 128 and AES 192 encryption but is not supported by many devices.
- Site-to-site server: this type is mostly used by large organizations or companies whose offices are in different locations. It helps connect one office network to another office network and establish a secure and private connection.
- Remote Access server: this type of VPN is suitable for both business and personal use. It allows users to connect to a virtual network from a remote location and gain access to all the resources and services of that network. The connection between the user and the VPN is completely secure and private.
Pros and cons of using a VPN
If you decide to use a VPN, here are some of the advantages you can enjoy:
- By masking your online activities, a VPN ensures that your ISP or the government cannot spy on your online activities.
- VPNs allow you to use public networks (Wi-Fi) securely. It hides your real IP address and provides a new one, which increases your privacy and anonymity online.
- By encrypting your data end-to-end, a VPN provides an additional layer of protection that helps safeguard your online activities and personal information. Encryption technology keeps hackers and cybercriminals at bay, making it difficult for them to steal your sensitive data.
- VPNs are compatible with a wide range of devices, including smartphones, tablets, and smart TVs, giving you more options for accessing online content.
- With a VPN, you can bypass geographical restrictions and access a wide range of streaming content and services from anywhere in the world.
Disadvantages of using a VPN:
- Good VPN services are not free, and you need to pay for a quality provider.
- If your VPN provider keeps logs, the authorities can retrieve them.
- A virtual network can slow down the speed of your internet connection.
- You may experience connection problems when using a free VPN.
- The level of protection depends on the software you use. You must choose secure software.
- A cached file may appear as expired if the cache expiration time is too long.
- VPNs may have slower speeds during peak times.
- Your activity may be resold to third parties.
The key differences between proxies and VPNs
Although both tools can help you hide your identity online and disguise your location, it’s important to note the difference between proxies and VPNs.
First of all, VPNs offer maximum speed, while with proxies it depends on the server you’re connected to. This means that VPNs are ideal for private use, while proxies are best for large-scale data collection for business purposes. However, proxies can sometimes be faster than a free VPN because they don’t encrypt your data.
Secondly, VPNs offer a strict encryption policy, while proxies have only a medium level or no encryption at all. This means that with a VPN, your data is protected at the highest level of security, making it virtually impossible for someone to access or intercept your online activities.
Thirdly, VPNs completely hide your IP address, while proxies only hide it from the destination site. In other words: While the owner of proxies can still see your IP address, with a VPN your activities are completely private and secure.
In general, the choice between VPNs and proxies depends largely on your specific needs and situation. Both VPNs and proxies can help you hide your identity on the Internet or disguise your location, but a VPN is the best choice if you want maximum privacy, security, and speed. Keep in mind that good VPN services are usually more expensive than proxies.
Below are some examples to help you decide when to use a particular tool.
Use proxies:
- If you want to filter out content unsuitable for children or restrict access to certain websites.
- If you want to access streaming content with local geographic restrictions.
- If you’re using an outdated operating system that doesn’t support modern VPN protocols.
- When you need limited anonymity, for example, when playing online games.
Use VPNs:
- If you want to ensure that all your online activities are encrypted and hidden from prying eyes.
- If you need to protect sensitive information from insider threats or theft.
- If you live in a country with strict censorship and surveillance and need to circumvent these restrictions.
- If you surf the Internet on a public WiFi network to protect your data and online activities.
Frequently Asked Questions
No, if you are already using a VPN, connecting to a website or application through a proxy is unnecessary. Both tools mask your IP address, but the VPN server also encrypts your data, providing more security.
Yes, you can use them together to add an extra level of privacy to your network. Remember that a stable Internet connection is crucial, and in most cases, there are no practical advantages to using two services at the same time.
How to Choose the Best Proxies?
When selecting a server for encryption or other purposes, you should consider the following selection criteria:
– Ease of use: choose software that is easy to use, and install and does not require additional knowledge.
– Traffic restrictions: Some servers block movie streams and peer-to-peer connections, which can limit your downloads.
– Connection speed: Servers can be slow, so you should test them first. If the server speed is good, you can pay for a server.
With our guide, you now know how to set up a proxy server that will hide your IP address, allow you to search anonymously, and give you access to restricted content. Regardless of what operating system you use, setting up this tool requires minimal effort, and the benefits of greater freedom, security, and privacy when browsing the Internet justify the effort.
