Demystifying Proxies: Unraveling Common Myths and Misconceptions

In our increasingly interconnected world, understanding the mechanisms that underpin our digital lives is no longer optional but necessary. One such mechanism is the often misunderstood concept of “proxies.” By definition, they are tools that can protect, anonymize, and optimize our online interactions. However, confusion often surrounds them, leading to numerous myths and misconceptions. In this article, we aim to demystify proxies, dispel common misconceptions, and illuminate their correct and legal uses.
Understanding the Concept of Proxies
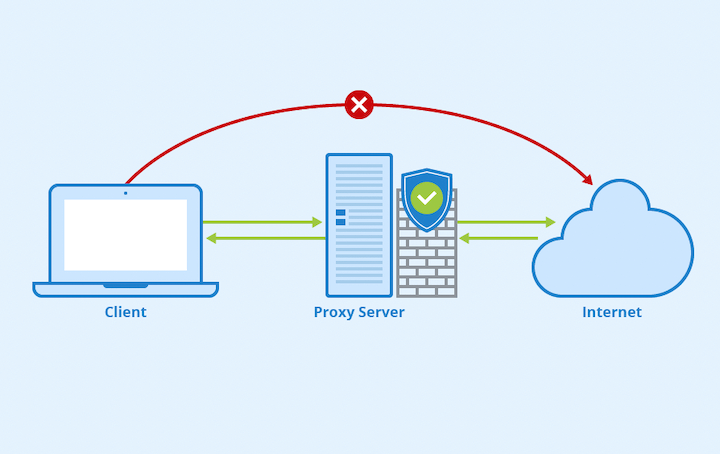
Definition and Functionality
A proxy server, simply known as a proxy, is a computer system or application that acts as an intermediary for requests from clients seeking resources from other servers. It enables a user to communicate with websites indirectly by forwarding requests and responses between a user’s device and the targeted website. When you use a proxy, your request goes to the proxy server first, which then interacts with the internet on your behalf.
Types of Proxies: Explained
There are several types of proxies, each with its unique features and uses:
- HTTP: These are the most common type of proxy servers. They work to process HTTP and HTTPS requests, which makes them a good fit for web browsing and accessing geo-blocked content.
- SOCKS: Standing for “SOCKet Secure,” these tools are more versatile than HTTP services as they can handle any type of internet traffic, not just HTTP or HTTPS. It makes them ideal for activities that involve different types of protocols, such as gaming, torrenting, or streaming.
- Transparent: As the name suggests, these services do not hide your IP address, thus providing no anonymity. However, they can be helpful in content filtering, as they intercept and redirect requests without requiring any configuration on the client’s side. Schools and businesses often use them to control internet usage.
- Anonymous: These intermediaries provide higher privacy as they hide the user’s original IP address from the web servers they interact with. However, they do identify themselves as proxies, meaning some websites might refuse to serve them.
- High Anonymity (Elite): These are the most private services. Not only do they hide the user’s original IP address, but they also do not identify themselves as proxies. It makes them less likely to be blocked by websites and provides the highest level of anonymity.
- Reverse: Unlike the other types of proxies used by clients (or end-users) to access the Internet, reverse proxies are utilized by servers to handle requests from clients on the Internet. Websites often adopt them to distribute incoming traffic among servers, providing load balancing and increased security.
Common Use Cases of Proxies
These tools are used in various situations, some of which include:
- Internet Privacy: Proxy services can mask your IP address, providing anonymity while browsing the internet. It can help protect your online activities from being tracked by third parties.
- Accessing Geo-Restricted Content: They can help bypass geographical restrictions on the internet by masking your actual location. For example, if a website is only available in a particular country, you can use a proxy in that country to access the website.
- Web Scraping: People often use these services as intermediaries in web scraping to collect data from websites without being detected or blocked. By routing requests through different proxies, scrapers can mimic the behavior of multiple users, making it harder for websites to identify and block them.
- Security and Control: In a corporate setting, one can apply proxy services to control employee internet usage. They can block access to specific websites or types of content, enhancing security and ensuring productivity.
- Load Balancing: Large websites often use reverse proxy services to distribute network traffic among multiple servers. It prevents any single server from becoming a bottleneck and ensures smooth performance even under heavy loads.
- Content Caching: Proxies can also store copies of frequently accessed web pages in their cache. When a client requests a cached page, the proxy can deliver it directly without contacting the web server. It can significantly speed up response times and reduce bandwidth usage.
- Testing and Debugging: Developers often use proxy services to simulate different network conditions and test how their applications behave under various scenarios. It can be critical for ensuring the robustness and reliability of the applications.
Common Myths and Misconceptions

The world of proxies is often clouded with myths and misconceptions, making it essential to distinguish fact from fiction. Let’s address some of these common fakes:
Myth 1: All Proxies are Illegal
Reality Check
Proxies, in and of themselves, are not illegal. They are tools used for various legal purposes. What determines the legality of a proxy’s use is the intent and action of the user.
Legal Uses
These technologies have numerous legitimate uses. Businesses often apply them to secure their internal networks and balance server loads. Individuals can utilize them to maintain privacy, access geo-restricted content, or manage Internet traffic for gaming or streaming. None of these uses are illegal.
Myth 2: Proxies Guarantee Anonymity
Reality Check
While proxies do provide anonymity by masking your IP address, they do not guarantee it completely. Some services, such as transparent proxies, reveal your original IP address to the destination server. Even anonymous and high-anonymity services can be detected and blocked by some servers.
Anonymity vs. Privacy
It’s essential to understand the difference between anonymity and privacy. While a proxy can provide anonymity by masking your IP address, it does not necessarily secure the data you send and receive. For this purpose, you would need additional security measures, such as encryption provided by a VPN or an HTTPS connection.
Myth 3: All Proxies are Slow and Unreliable
Reality Check
Not all services are slow or unreliable. The performance of a proxy can vary significantly based on several factors. For instance, a high-quality, paid proxy will likely provide better speed and reliability than a free one.
Factors Impacting Proxy Speeds
Factors that can impact the speed and reliability of a proxy include the quality of the proxy server, its location relative to the user and the target server, and the amount of traffic it is handling. Using a proxy geographically close to the target server and not overloaded with traffic can help improve speed.
Myth 4: Proxies and VPNs are the Same
Reality Check
While proxies and VPNs can provide privacy and help bypass geo-restrictions, they are not the same. There are critical differences in how they work and the level of security they provide.
Differentiating Proxies from VPNs
A proxy only reroutes your traffic for a specific application or browser. In contrast, a VPN (Virtual Private Network) forwards all your internet traffic and typically offers higher security through encryption. Thus, a VPN is better if you want complete privacy and security. However, a proxy might suffice for bypassing geo-restrictions on a particular website.
Responsible Usage of Proxies
Even though proxies can be a potent tool in your digital arsenal, it’s crucial to understand their appropriate use, potential misuse, and general safety tips.
Appropriate Applications
The primary purposes of these technologies include maintaining privacy, accessing geo-restricted content, handling server requests for large-scale websites, web scraping, testing and automation, and protecting internal networks. Proxies can help users anonymize their online presence, control network traffic, and improve performance.
Potential Misuses and Risks
However, the potential for misuse does exist. One can exploit proxy services for illicit activities, like unauthorized data scraping, cyberattacks, or evading law enforcement. Such abuses are illegal and unethical. Furthermore, not all services provide the same level of security. Free or poorly managed proxies can pose risks, including exposure to malware, unauthorized data access, or even identity theft.
Tips for Safe and Effective Proxy Use
To use proxies safely and effectively, follow these tips:
- Choose a Reputable Proxy Provider: If you are paying for a service, ensure it’s from a reputable provider. Research the provider, read reviews, and understand their privacy policies before committing.
- Understand the Limitations: While proxy services can provide anonymity, they don’t offer complete security or privacy. Consider using additional security measures, like VPNs, secure browsing techniques, and intermediary tools.
- Be Aware of the Laws and Regulations: Ensure that you are not breaking any laws or violating any terms of service when using a proxy. Remember, using these technologies for legitimate purposes is legal, but their misuse can have serious consequences.
- Use HTTPS: Always use secure HTTP (HTTPS) when transmitting sensitive data, even when using a proxy. It encrypts your data and adds an extra layer of security.
- Avoid Free Proxies for Sensitive Tasks: Avoid free ones if you’re handling sensitive data or require reliable service. They tend to be less reliable and may lack security. Reputable and paid services are generally safer and more dependable for serious tasks.
Conclusion
Understanding the role of proxies is vital in our digital lives. As we have debunked, they are not illegal tools, do not guarantee absolute anonymity, are not inherently slow or unreliable, and are distinct from VPNs. The key is to use proxy services responsibly, with an understanding of their functionalities and limitations. As our digital footprint continues to grow, so will the role and importance of intermediary tools. The future will undoubtedly bring more sophisticated proxy services, continuing to shape our online experience in unprecedented ways.
