Understanding Proxy Chains: A Detailed Exploration of Their Mechanism and Usage
As the call for enhanced digital privacy grows louder, advanced measures like proxy chains are emerging as critical resources for users in the digital world. But what exactly are these technologies, and how can they help enhance anonymity online, bypass geo-restrictions, and fortify cybersecurity measures? This article unravels the complexity of proxy chains, elucidating their operational mechanisms and applications.
Understanding Proxy Chains
Explanation of a Single Proxy
A single proxy acts as an intermediary between a user (client) and the desired web service (target server). When a client requests to access a website, the request goes through the proxy server instead of connecting directly to the website’s server. This process masks the client’s identity from the target server, making it appear that the proxy is the request’s origin.
Detailed Definition and Explanation of Proxy Chains
A proxy chain extends the concept of a single server. Instead of one server, the client’s request travels through multiple proxies. Each server in the row only knows the identity of the server before it and the one after it, making it nearly impossible to trace the original request back to the client. Only the last server interacts directly with the target server, thus providing the user with an additional anonymity level.
How Do Proxy Chains Work?
When a client sends a request, the first server in the chain receives it. It then forwards the request to the second proxy, and this process continues until the last server communicates with the target. The target server’s response then travels along the same route, reaching the client without revealing the client’s original IP address to the target server.
Different Types of Chain of Proxies
One can classify these technologies depending on how proxies are selected and organized. Each type offers varying levels of flexibility, predictability, and anonymity.
- Strict Chain: It involves a fixed sequence of proxies. The order and the number of proxies remain constant for every request. This type is easy to set up but offers less unpredictability.
- Dynamic Chain: In the type, the proxies involved in routing requests can change with each request. It could depend on the availability, performance, or a specific algorithm that decides which proxies to include in the chain. For instance, if one proxy is not responding, it will be skipped, and the chain will use the following server instead. This type offers more flexibility and resilience against technical failure but might be more complex to set up.
- Random Chain: This type is the most unpredictable because it changes the proxies involved with each request and their order. When a request is made, the servers are randomly selected and arranged. A user can also set up the number of proxies to use. This type offers the highest level of anonymity but could also lead to slower request times due to the constant change in services and their geographical locations.
- Mixed Chain: This type combines the characteristics of simple, dynamic, or random chains. It allows for a certain level of customization, allowing users to decide which part of the chain should be static, dynamic, or randomly arranged. It offers the most flexibility and can cater to specific needs, but it is also the most complex to set up and maintain.
The Components of a Proxy Chain
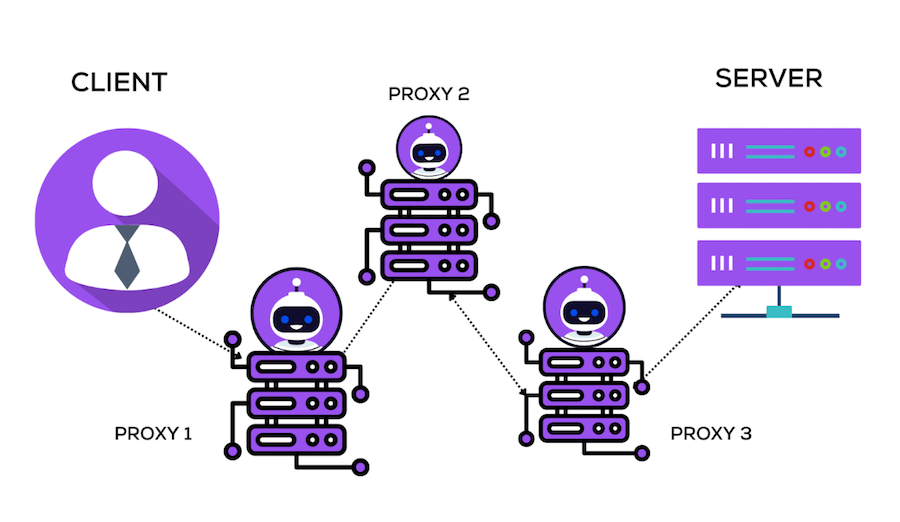
A proxy chain comprises three major components: the client, the proxy servers, and the target server. Each plays a unique role in maintaining security and privacy.
Client
The client is the user or system initiating the request. It could be a person browsing the internet or an automated system requesting an API. The client connects to the first server in the chain and initiates the request to access data from the target server.
Proxy Servers
These servers are the core components of a chain. These are intermediary servers that relay requests from the client to the target server. In a chain, multiple proxy servers typically pass the client’s request along the chain. Each server only knows the IP addresses of the server before it and the server after it, ensuring that the client’s original IP address is hidden from the target server.
Target Server
The target server is the final destination of the client’s request. It could be a website, an API, or any other online service the client wants to access. The target server receives the request from the last server in the chain, processes it, and sends a response back to the client through the same route. Because of the proxy chain, the target server is unaware of the request’s source, which helps maintain the client’s privacy and anonymity.
Benefits and Uses of Proxy Chains

The use of this technology offers numerous benefits and has several applications. These extend beyond merely providing anonymity and privacy, touching on aspects such as geographical restriction bypass, enhanced security, and more.
- Anonymity and Privacy
The primary benefit of using the technology is the enhanced level of anonymity and privacy it offers. Thus, each hop further obscures the request’s source, making it difficult for the target server or intermediary to determine the client’s IP address.
- Bypassing Geographical Restrictions
You can use the technology to bypass geographical or IP-based restrictions. It becomes possible since the final proxy in the chain, interacting with the target server, could be in a different geographical location than the user, hence appearing to the server as a legitimate local user.
- Increased Security
These technologies increase security by making it more difficult for malicious actors to attack a client directly. Since the client’s IP address is hidden behind multiple proxies, attackers can’t easily find or target the client’s machine.
- Load Balancing
In larger networks, these technologies can help in load balancing. Distributing requests across multiple servers ensures that no single server is overwhelmed with too much traffic, so potentially improving performance and stability.
- Data Scraping
The chains are also used in web scraping activities to prevent being blocked by the target server. By regularly changing the proxies used in the chain, scrapers can mimic the behavior of multiple distinct users, making it difficult for the target server to detect and block the scraping activity.
- Other Use Cases
Here are some other common use cases for chain technologies:
- Anonymous communication for journalists and whistleblowers;
- Research on competitive intelligence where a business doesn’t want to reveal its IP to competitors;
- Testing network intrusion detection systems for resilience against complex proxy-based attacks.
Each application capitalizes on the anonymity, geographic flexibility, and enhanced security these technologies provide.
Limitations and Risks of Using a Chain of Proxies

Despite their many advantages, these technologies also have their downsides. Knowing these limitations and potential risks is crucial before implementing these technologies.
- Decreased Speed
Using the technology can significantly decrease internet speed. The client’s request and the server’s response must travel through each server in the chain, increasing the time it takes for data to be sent and received. This delay is even more pronounced when proxies are located in different parts of the world.
- Legal and Ethical Issues
While using a chain of proxies for legitimate privacy and security reasons is generally acceptable, they can also be misused for illicit activities such as hacking or illegal content access. Depending on the jurisdiction, using the technology to circumvent regional restrictions or mask one’s identity may be legally and ethically questionable.
- Dependability and Stability Issues
The reliability of a chain of proxies is as strong as its weakest link. The whole technology can collapse if any component fails, resulting in failed requests. Therefore, maintaining a stable technology requires constant monitoring and maintenance to ensure all proxies function correctly.
- Data Security Risks
While using this technology can enhance privacy by hiding the client’s IP address, it can also pose data security risks. If servers in the chain are compromised, the data passing through them could be intercepted and altered. Therefore, we recommend always encrypting sensitive data before sending it through a chain.
Choosing the Right Proxy Chain
Selecting the suitable technology and provider is a decision that hinges on multiple factors, including speed, location, security level, and the nature of your requirements. Also, it’s essential to consider the different providers available in the market and the cost implications.
Considerations: Speed, Location, Security Level, Etc.
The ideal technology choice can vary depending on individual needs and specific use cases. Speed is critical for those seeking to maintain smooth browsing or streaming experiences, so a proxy chain with fewer nodes or geographically closer proxies might be ideal. If bypassing geographical restrictions is the primary goal, you should choose proxies in the desired country. Additionally, selecting a technology with more nodes or using random chains would be better suited for those requiring high-level security and anonymity.
Different Providers and Their Offers
Numerous providers in the market offer a range of proxy chains, each with its features, benefits, and drawbacks. Some providers may specialize in technologies with high-speed proxies for seamless streaming, while others may focus on providing high-security technologies for enhanced anonymity. It’s essential to thoroughly research and compare different providers to find the one that best suits your needs.
Free vs. Paid Proxy Chains
While free proxy chains can be tempting, they often have drawbacks such as slow speeds, unreliable uptime, and questionable security. On the other hand, paid technologies generally offer better performance, more reliable uptime, and better security measures. Some also provide customer support, custom configuration options, and other premium features. However, the cost can vary significantly, so balancing your needs against your budget is crucial.
Setting up a Proxy Chain

Implementing this technology may seem daunting, but you can do it efficiently with a step-by-step guide and the right tools. Also, adhering to some best practices can help maintain the chain effectively.
Step-by-Step Guide to Setting up a Basic Proxy Chain
- 1. Select Your Proxies: Choose proxies that align with your speed, location, and security needs. Remember the chain type (strict, dynamic, random, mixed) you want to create.
- 2. Configure Your Proxies: Input the IP addresses and port numbers of your chosen proxies into the proxy chain software or tool you use. Make sure to arrange them in the order you want the requests to be routed.
- 3. Test Your Chain: Use online tools to test whether your technology works correctly. You can check your visible IP address to verify that your actual IP is being masked.
- 4. Make Adjustments: If needed, adjust the order of your proxies or substitute underperforming proxies for better ones.
Tools and Software Required
Various software and tools are available to help set up and manage a proxy chain. ProxyChains or Proxychains-ng for Linux systems and Proxifier for Windows or MacOS are popular. These tools allow you to input your chosen proxies, configure the chain, and route your internet traffic.
Best Practices and Tips for Maintaining a Proxy Chain
- Monitor Your Proxies: Keep a regular check on the performance of your proxies. Remove any that are underperforming or causing latency issues.
- Update Your Chain Regularly: The availability and performance of proxies can change over time. Regularly updating your proxy chain ensures optimal performance.
- Security: Always encrypt sensitive data before sending it through a chain of proxies. It adds an extra layer of protection in case any services are compromised.
- Balancing Speed and Anonymity: Adding more proxies to your chain increases anonymity but decreases speed. Find a balance that suits your needs.
Remember, setting up and maintaining this technology requires some technical expertise and ongoing management, but the privacy and security benefits can be significant.
Case Study: Practical Applications of Proxy Chains

Let’s consider three case studies to provide a practical perspective on how these technologies are used, each demonstrating a unique application case.
Case Study 1: Data Scraping
A market research company needed to scrape vast amounts of data from multiple websites for analysis. However, they frequently faced IP blocking issues due to the high volume of requests from their single IP address. They decided to implement a dynamic proxy chain with rotating proxies. It allowed them to distribute their requests through multiple IP addresses, reducing the chances of being detected and blocked. It resulted in more efficient data scraping with fewer interruptions, providing them with the data they needed for their research.
Case Study 2: Security Enhancement
A large corporation was concerned about the potential for cyber attacks targeting its internal systems. They implemented a proxy chain for all outbound internet connections from their systems. This way, their IP addresses remained hidden, making it difficult for potential attackers to locate and target their systems. The company also encrypted its data before sending it through the chain, further enhancing security.
Case Study 3: Bypassing Geo-Restrictions
A content reviewer working for an international media company needed to access region-locked content from various countries. By using a chain of proxies with servers located in those specific countries, they could bypass the geographical restrictions and view the content as if they were in that country. It allowed the content reviewer to perform their work despite the geo-restrictions efficiently.
These case studies demonstrate that these proxy technologies can be valuable in various situations, from enhancing security to enabling data access beyond geographical boundaries.
Final Thoughts
Proxy chains are a potent tool for enhancing online privacy and security, bypassing geographical restrictions, and much more. However, they are not without limitations, and their use should always align with legal and ethical considerations. As with any tool, their effectiveness largely depends on the user’s understanding and correct application. So, whether you’re an individual seeking increased internet privacy or a business exploring data scraping opportunities, proxy chains, when used correctly, can provide a remarkable solution.
