Transparent Proxy Server — Easy Explanation

Through my years in cybersecurity, the term “transparent proxy” often popped up and captivated my attention. But have you ever wondered what these services actually are? My quest has led me through rigorous tests, deep dives, and enlightening discoveries. Today, I’m poised to guide you through this very revelation.
Indeed, transparent proxies have a longstanding role. But why “transparent”? And what sets them apart from other similar services? Let’s embark on this enlightening voyage, transforming ambiguity into clarity.
What is a Transparent Proxy?

At its core, a transparent proxy is an intermediary between the user and the internet. This service steps in when you send a request. For example, when you try to access a website, the service processes this request and forwards it to the intended destination.
Now, how do transparent servers handle your data? Essentially, they don’t modify your IP address or any other data. They’re like clear windows, allowing light (or, in this case, data) to pass through without significant alteration.
One of the marvels I’ve discovered in my tests is their interaction with the cache. These servers often store frequently accessed web pages. So, when you request a page in their cache, they swiftly deliver it — no need to fetch it from the original server.
Pros
Transparent services come with many benefits. Let’s list a few main ones.
Speed and Efficiency
These days, every millisecond matters, and these proxies ensure your web requests zip through without delay. Here’s how they excel:
- Reducing Latency: My tests consistently show that these proxies streamline internet traffic flow. Acting as an intermediary, they quickly process and forward requests to minimize lag.
- Caching Benefits: As I highlighted earlier, their ability to interact with cache is a game-changer. They store copies of frequently visited web pages. It allows them to serve this content instantly later and eliminates the need to repeatedly fetch it.
- Load Balancing: I’ve seen these proxies adeptly distribute incoming traffic across several servers in larger network environments. It prevents any single server from overloading, enhances overall performance, and minimizes downtime.
Ease of Setup
Having experimented with various proxies, I can confidently say that transparent servers are among the easiest to set up. The thing is that they require far less tweaking than other types. They’re often almost a plug-and-play setup so you can use them immediately. Given their straightforward nature, I recommend this type to novices and enterprises seeking a simple yet effective solution.
Scalability
Whether for a burgeoning business or an individual with fluctuating needs, this proxy type offers the agility to scale your infrastructure up or down effortlessly. I’ve managed expansions where we’ve scaled the proxy setup to handle increased traffic smoothly, and the transitions have always been seamless.
One other highlight of working with type is versatility. These services handle everything from sudden spikes in web traffic to planned capacity increases. Plus, they are suitable for various needs.
Cons
However, transparent web connections also have their pitfalls. A significant drawback is the lack of anonymity. Because these proxies do not modify your IP address, your original IP is still exposed to the destination server. It can be a deal-breaker for users who prioritize privacy and want to keep their internet activities under wraps.
Additionally, while the caching feature speeds up access to popular sites, it can lead to issues accessing the most up-to-date content. Sometimes, this proxy might serve an older version of a webpage from its cache instead of retrieving the latest version. This lag can be critical when you access sites that frequently update their content, like news portals or financial markets.
Examples of Transparent Proxies
Transparent web connections are ubiquitous yet often go unnoticed due to their seamless integration into various networks. For instance, consider a large educational institution where internet access must be monitored and filtered without disrupting hundreds of simultaneous users. Here, a proxy can filter content and track web usage while providing a fast connection. Plus, the end users won’t realize it’s there. Sounds like magic?
Besides, this proxy type is frequently used in corporate settings to enforce company policies regarding internet access and secure data transmissions. They sit quietly between company devices and the internet, examining outgoing requests. This ensures that sensitive information remains within the business’s secure perimeter.
Why to Use Transparent Proxy

By now, I’ve witnessed a spectrum of outcomes with proxies. Let’s discover some use cases and when these services shine the brightest.
Cases of Use
- Content Filtering: Transparent web connections are invaluable for organizations that enforce internet usage policies without altering user experience. They can block access to non-business-related sites or those deemed inappropriate without requiring individual device settings.
- Data Monitoring and Bandwidth Control: These proxies are watchdogs for companies concerned about data leaks or excessive bandwidth usage. They monitor outgoing and incoming data and provide detailed reports on usage patterns.
- Improved Network Performance: By caching frequently accessed web pages, transparent services reduce load times and save bandwidth. This caching also reduces the strain on network resources, essential in environments with heavy web traffic, such as universities or large businesses.
- Regulatory Compliance: In industries where data handling and privacy are regulated, these proxies help enforce compliance with laws such as GDPR or HIPAA. They ensure that all data passing through the network adheres to legal standards. It allows to avoid hefty fines and maintain customer trust.
Setting Up a Transparent Proxy: A Step-by-Step Guide
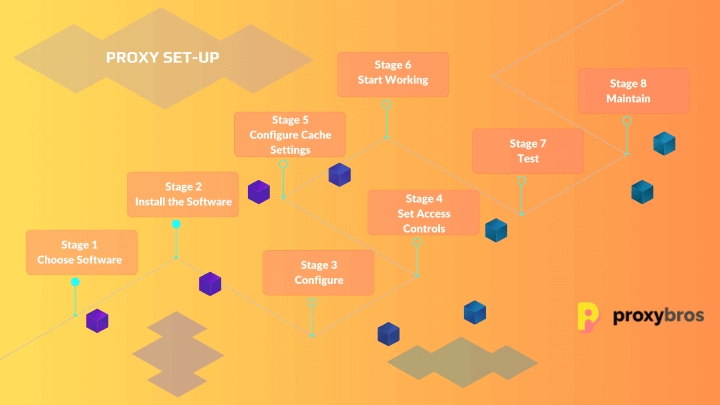
Step 1: Choose Your Software
There are multiple proxy services, so you can get baffled. But fear not! These are the main things to keep in mind:
- Purpose & Needs: First, define what you need the proxy for. Are you looking for better security and speed? Or anything else? Make your choice!
- Reliability: Choose services that offer solid stability. The last thing you want is a proxy that crashes during critical moments.
- Features: If you need specific features, double-check if your service offers them. It could include caching capabilities, support for particular protocols, or advanced security features.
If you struggle with the final decision, I welcome you to my all-in-one guide for choosing the best proxy for your needs.
Step 2: Install the Software
Installing transparent network proxy for Apple system services:
- Update your system packages in Debian or a Debian-based Linux distribution using the two commands: sudo apt-get update & sudo apt-get upgrade.
- Install your chosen proxy software using the appropriate command.
Installing on a Windows system:
- Visit the official website of your software and download the Windows installer. Most providers offer .exe or .msi files for Windows.
- Navigate to your download folder and double-click on the installer file.
- Follow the on-screen instructions to complete the installation.
Step 3: Basic Configuration
Access the configuration file to set basic parameters like the port you want the proxy to listen on.
Step 4: Set Access Controls
Set access control lists (ACLs) to allow specific devices or networks to use the proxy. This way, you ensure that only authorized users or devices can access it.
Step 5: Configure Cache Settings
Set up cache parameters in the configuration file to improve speed and efficiency for frequently accessed data.
Step 6: Start and Enable the Proxy
Once you’ve configured the settings, you can use your service with an appropriate command.
Step 7: Test, Test, Test!
Now, test your service! Access a website to ensure it’s working correctly.
Step 8: Regular Maintenance
Remember to periodically check for software updates, review your configuration settings, and ensure your cache is managed effectively.
Transparent Proxy VS Non-transparent — The Key Differences?
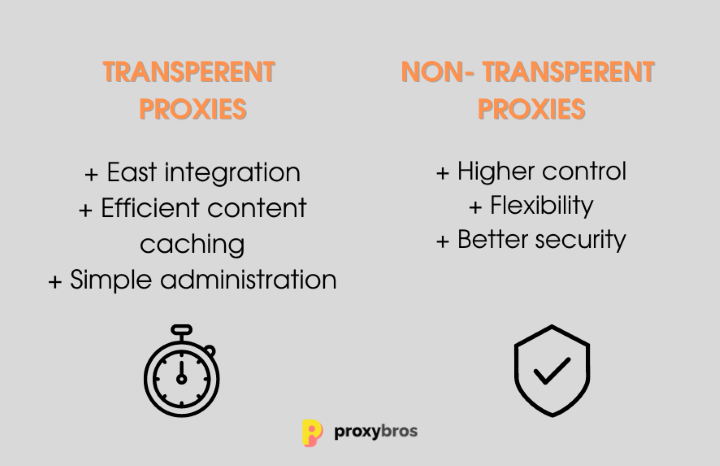
Now that you know what transparent proxies are, let’s move to the next group — non-transparent services. This versatile proxy group is also known as explicit proxies. They often require manual configuration on each device. Users must adjust their network settings to route traffic through them. Thus, they are overall more visible and sometimes cumbersome to implement. At the same time, this explicit setup allows for more controlled access but can be a barrier regarding ease of use and user compliance.
In essence, the choice between transparent vs non transparent proxy services hinges on the balance between ease of administration and user awareness. Transparent proxies excel in environments where user transparency is key, while their opponent servers are better suited where explicit control and user acknowledgment are desired.
Conclusion
As we wrap, it’s clear that transparent proxies blend simplicity, efficiency, and control. This unique combination makes them indispensable for both personal and professional usage. So why ponder? If you’re looking for a beginner-friendly server with excellent features, this type can be your best choice!
FAQ
It acts as a gateway between the user and the internet, processing requests and forwarding them anonymously to their destinations.
It offers speed through caching, simplified network management, content filtering, and seamless integration that doesn’t disrupt user experience.
You can use advanced network diagnostic tools or specific proxy detection websites to identify if your internet traffic is being routed through a proxy.
These include internet usage monitoring, content filtering in institutions, bandwidth management, enhancing network performance by caching, and enforcing security policies in corporate environments.
Even though these services enhance security by filtering and monitoring traffic, they don’t anonymize users. This happens because the original IP address remains visible to destination servers. If privacy is a primary concern, this could potentially impact user privacy.
