TLS Termination Proxy Explained: What Is It And How Does It Work?
TLS Protocol: TLS Meaning and Principle of Work
Meaning
The Internet is based on data exchange and processing. To process and exchange it correctly, computers use sets of rules in accordance with general standards. These guidelines are called network protocols. Network protocols explain to the computers on the World Wide Web how to communicate with each other.
TLS (Transport Layer Security) is an encrypted protocol for secure data transactions. In 1999, the IETF( Internet Engineering Task Force) organization released the first version of TLS as an upgrade to the SSL 3.0 standard.
SSL standard was initially an invention of Netscape Corp., aimed to secure the unencrypted vulnerable HTTP hypertext transfer protocol.
In 2015 SSL standard was declared obsolete. Later, TLS replaced SSL almost entirely. In 2022 TLS 1.3 will be the most modern and advanced security protocol.
TLS In The OSI Model
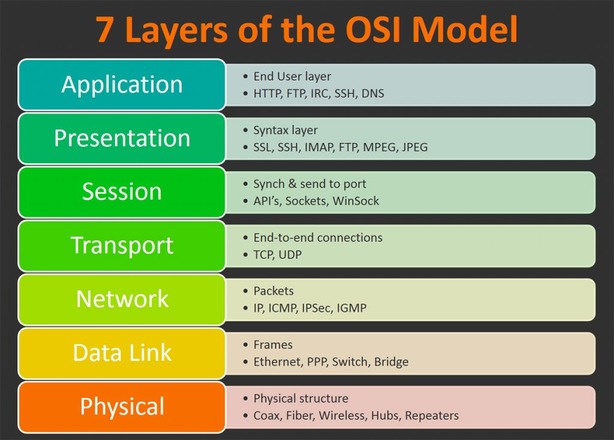
The OSI (Open Systems Interconnection) model gives the first approximation of the protocol’s scope.
A simple protocol can belong to one OSI level. Complex protocols have various features, so they belong to different OSI levels at the same time.
TLS has the features of four levels: application, presentation, session, and transfer.
- Application layer: communication with user-facing applications.
- Transport level: data transaction.
- Presentation level: encryption.
- Session level session resumption.
How TLS Works
HTTP is the main data transaction protocol on the Internet. Initially unsecured, it became safe to use with SSL/TLS encryption.
TLS works as an encryption security add-on to HTTP. It sets the connection rules and calls cryptographic systems to secure the connection. The upgraded HTTP version is widely known as HTTPS.
TLS sets three main security goals:
- Confidentiality
- Integrity
- Secure authentication
The implementation of these goals is the essence of TLS principles of work.
Confidentiality
Confidentiality protection is a combination of actions aimed at avoiding unwanted information access.
Example of a system without confidentiality protection:
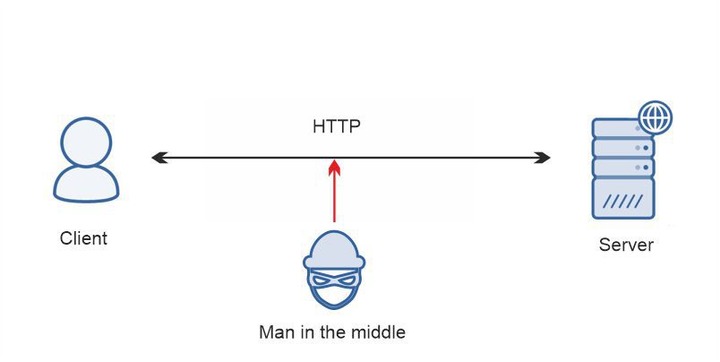
- 1. A user wants to log in to a bank website.
- 2. A user connects to a bank server with a client machine.
- 3. A client sends a message with bank credentials.
- 4. A server checks the login and password and lets the user in.
The confidentiality is under threat! An attacker (“man in the middle”) can intercept the message and read the content.
Example of a system with simple symmetric encryption:
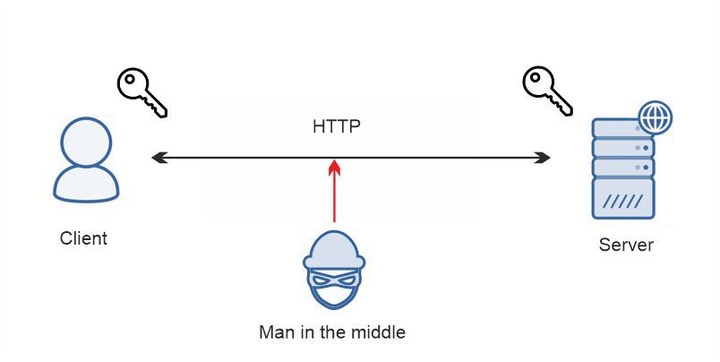
A client sends a message with bank credentials to a server. Meanwhile, a client encrypts the message with a key before sending it. This task is more difficult for a man in the middle to solve, but it is still possible to grab the message and decrypt the content.
TLS Secure Encryption
TLS protocol uses a more secure asymmetric type of encryption. It starts a mutual verification process between a client and a server. This process is called a handshake. The protocol can call different algorithms to perform the handshake, but RSA and Diffie-Hellman algorithms are the most popular. This is a simplified example of an RSA handshake.
A server holds two keys instead of one for each connection: public and private. Anyone can view a public key. However, a message encrypted with this key can be decrypted only with a private key. A server keeps this private key and does not share it with anyone.
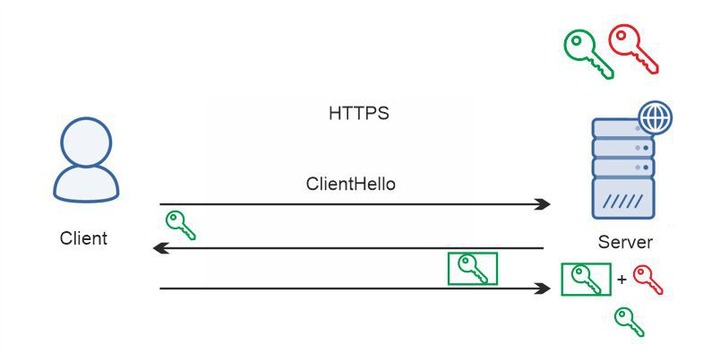
- 1. A client connects to a server and requests a secure connection.
- 2. A server responds and sends a public key to a client.
- 3. A client encrypts the data with this key and sends it back. Even if attackers grab the message, they cannot decrypt it without a private key.
- 4. A server gets a message and decrypts it with the private key.
Integrity
Data integrity protection is a set of measures for keeping information unchanged. The main goal is to avoid info corruption due to system malfunctions.
TLS uses symmetric hash functions (MD5, SHA, etc.) to reach integrity:
- 1. A client converts a data array into an encrypted string and gets a hash.
- 2. A client sends data and hashes packed together.
- 3. A server receives and extracts the data and the hash. It converts the data to hash again and compares the extracted hash with a recently received hash. If they do not match, it means that the message is corrupted.
Authentication
Authentication protection means an authenticity check. For example, a client connects to a bank. A man in the middle redirects a client to a similar website to steal the client’s credentials.
Digital certificates help to check if the server is trusted. A server can certify its public key with trusted institutions called Certificate Authorities(CA). These are the companies like IdenTrust, DigiCert, and GoDaddy. They certify a public key with a Root CA certificate. When a client machine connects to a server and gets the key, it appeals to the CA and asks: is this key genuine? If a key is not certified, CA will block the connection.
TLS Proxy: What Is It and How Does It Work
What Is A Proxy?
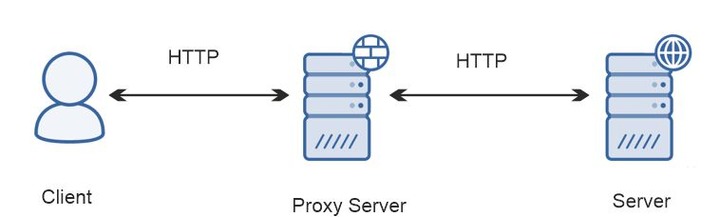
A proxy is an intermediary between a client and a server. All the traffic passes through an intermediary. The benefits of an intermediary point connection are:
- Load balancing
- Identity hiding
- Protection from intrusion, tracking, and malware
- Traffic filtering
- Bandwidth saving
How TLS Proxy Works
TLS proxy for Windows, Mac, or Linux is the way to manage HTTPS traffic. It works as an intermediary server like other proxies. The difference is it works within the HTTPS tunnel, which secures the information using the handshake algorithm. Thus, this intermediary has to participate in encrypted data exchange.
There are two types of TLS proxies based on how they participate in this process. Passthrough proxies forward the message from a client to a server and backward. Termination proxies interrupt the connection in the middle.
TLS Termination Proxy
Types of TLS Termination Proxy
TLS termination proxy is an active participant in the connection. It routes HTTPS traffic from client to server and interrupts the connection to read and analyze the traffic. To do that, an intermediary breaks the tunnel between a client and a server into two parts: Client-Proxy, Proxy – Server. TSL connection stops on one side. There are two types of connections depending on the side:
- Offloading: “Proxy-Server” connection terminated. An inbound HTTPS data from the client’s side is forwarded as HTTP to a server.
- Encryption: “Client-Proxy” connection terminated. An inbound HTTP data from the client’s side is forwarded as an HTTPS to a server.
- Bridging is a combination of two types of connections.
Offloading
Offloading type is the most common one in network building.
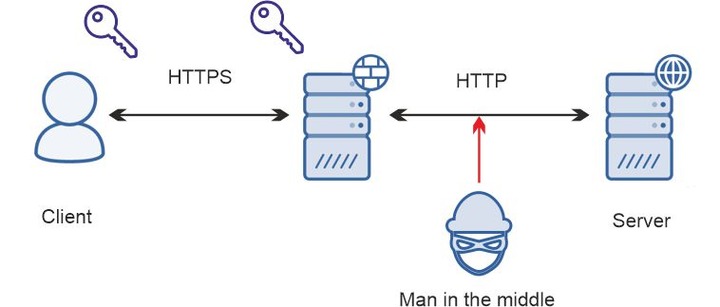
A proxy server receives an encrypted message (HTTPS) from the client’s side and decrypts it. As proxies can work with decrypted files only, at this point, they can analyze and manage the data. For example, it can balance the load for the backend, allow network surveillance, and block malicious activities. Then an intermediary forwards the traffic to a server using HTTP.
When a server responds, the intermediary receives the message again. At this point, it can also allow data analysis and enable useful functions: malware and intrusion detection, content filtering, and enabling additional versions of protocols. Then a proxy encrypts the data again and sends it to the client.
As an intermediary does all the encryption and decryption work – it offloads the servers, so they can work faster.
The great disadvantage of this method is an unsecured part of the tunnel with HTTP traffic. A man in the middle can get access to the data there and steal it. Fortunately, there are no other vulnerabilities – a man in the middle can’t create a gateway to steal information.
To start the termination process, a proxy server needs to have a certificate of the same type any server gets from CA. A server within the TLS tunnel needs to prove it is trusted to start the handshake process – and this is what the termination intermediary does.
Encryption
The encryption type is similar to offloading, but the data is encrypted from the server side. An intermediary receives plain text client data (HTTP). Then it encrypts the traffic and forwards it to the server with HTTPS. A server responds, and an intermediary decrypts the data and forwards it to the client.
Bridge
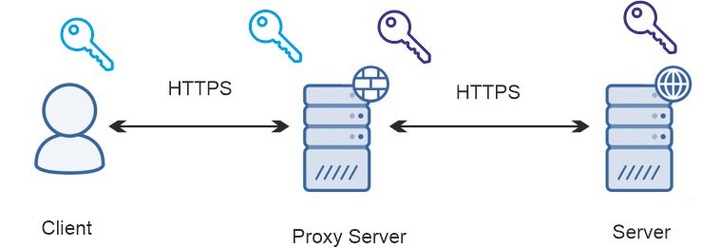
This type establishes an encrypted connection on both sides. The first proxy gets data from the client. A client and a proxy do a handshake. An intermediary decrypts the data from the client and runs the necessary applications: malware filtering, load balancing, and HTTP varnish. Then the intermediary encrypts the data again – now for the handshake with a server. It sends data, receives a response, decrypts it, and optimizes it again. Then it encrypts the information to send it to the user.
In other terms, a proxy interrupts the connection, but the traffic remains encrypted. The traffic gets decrypted at the midpoint, so the data can be compromised if an intermediary has vulnerabilities.
The Reasons for Using Proxy Termination
- 1. To make HTTPS communicate with HTTP (Helps to base the connection of the frontend HTTPS with a backend HTTP).
- 2. To add a certificate-based authentication point.
- 3. To offload servers.
- 4. For load balancing.
- 5. To enable features not accessible with the data encrypted: data analysis, malware & intrusion detection, content filtering, and HTTP varnish.
- 6. Enable additional protocol versions.
- 7. If a proxy is much closer to the client than an endpoint, the handshake process is faster.
Pros and Cons of Using a Proxy Termination
Pros
- Allows HTTPS to communicate with HTTP
- Offloads servers
- Not very expensive
- Efficient load balancing
- Data analysis
- Allows actions on the traffic
- Network surveillance, intrusion detection
- Allows to enable HTTP accelerator
Cons
- Vulnerable to man-in-the-middle attacks
- Not suitable for important networks
- A bottleneck at the midpoint if you have lots of backend servers
TLS Passthrough Proxy
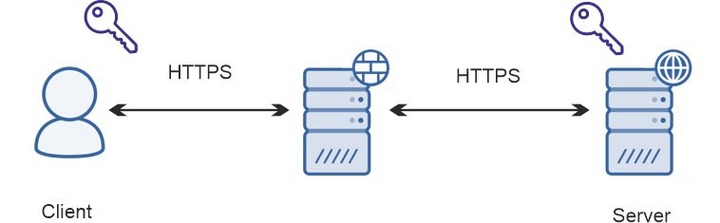
A passthrough proxy is a passive participant in the connection. It ‘sits’ between a client and a server and forwards the encrypted message from one to another without any intervention or decryption in the middle. All the data is decrypted only at the endpoints. This connection type offloads the intermediary and allows it to perform load balancing more accurately.
The end-to-end passthrough tunnel is safe because a secure HTTPS connection does not turn into HTTP like in the termination process. A man in the middle cannot access the protected data at any part of the tunnel.
The disadvantage of this method is its high cost and the inability to perform any action on web traffic.
The Purposes of Using Passthrough Proxy
- A proxy encapsulated in HTTPS traffic.
- More accurate load balancing
- A secure connection on all parts of the path.
- Protection from “man in the middle” attacks.
Pros and Cons of Using a Passthrough Proxy
Pros
- Provides a stable channel for HTTPS-HTTPS connection
- Does not need a certificate
- Not vulnerable to man-in-the-middle attacks
Cons
- Expensive
- No caching
- No data analysis
- No actions on traffic
Summary: TLS Termination Edge VS Passthrough Proxies
TLS termination and passthrough proxies have both their pros and cons. However, it is not possible to say what type is better. Termination and passthrough proxies pursue different goals. A brief summary shows the differences between these types, and their pros and cons.
| Termination | Passthrough | |
| Characteristics | ||
| Network design | Intermediate gateway | End-to-end |
| Data encryption/decryption | At mid-point | At endpoints |
| Participation in the handshake process | Active | Passive |
| Connection structure | HTTPS-proxy-HTTP | HTTP-proxy-HTTPS |
| Additional security measures | Requires certificate | Does not need a certificate |
| Features | ||
| HTTP-compatible | Yes | No |
| Security | Vulnerable to man-in-the-middle attacks | Secure |
| Proxy features efficiency | High | Limited |
| Offloads backend | Yes | No |
| Cost | Less expensive | More expensive |
