Why Are Traffic Generation Proxies Popular?
Transform your online presence and fend off competitors with seemingly endless fake web traffic. In this comprehensive guide, we dive into the world of proxies and explain the different types of proxies, including CDNs, VPNs, and web proxies, and how they can be exploited by scammers.
Learn how they are used by scammers, what dangers they pose, and what steps you can take to determine whether certain web actions are valid or not. Finally, we’ll give you practical tips on how to detect and effectively neutralize threats to protect your business initiatives.
What Is A Proxy?
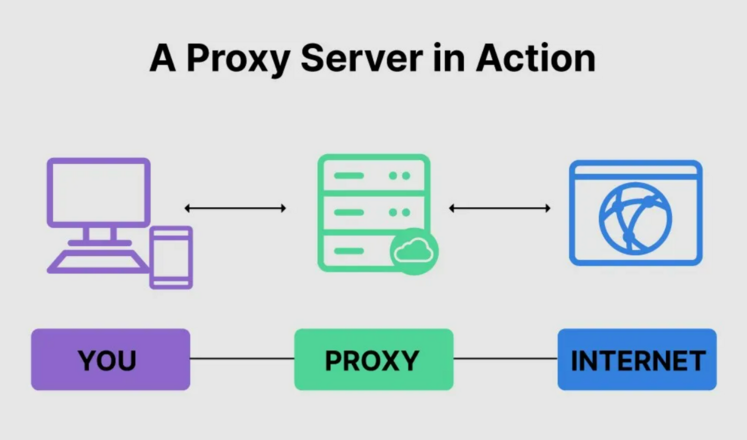
A proxy is a technology that serves as an intermediary between devices. With their unique IP address, such servers enable users to obscure their true location and identity. Proxies are used for several purposes, including ensuring anonymity, verifying downloads, filtering web content, accessing content from other countries, and bypassing regional restrictions.
If your website receives an excessive web flow, the servers may not be able to handle the load, which can lead to a crash. However, proxy servers can mitigate this problem by using load-balancing techniques that distribute traffic to the nearest server and reduce the load on a server.
Online criminals must be cunning to succeed in ad fraud, form hacking, web scraping, and other malicious activities. To circumvent the strict security measures in place on many websites, these attackers resort to mimicking the behavior of real site visitors.
One of the most common methods to achieve this goal is the use of proxy servers, which allow attackers to hide their true identity and present themselves as harmless actions from another, less suspicious server or location. For example, proxies are commonly used in click fraud attacks, where the process is automated by repeatedly changing the IP address to simulate multiple users clicking on an ad in rapid succession.
However, proxy servers are not harmful per se. Just as some legitimate users disable JavaScript, they can use VPN to protect their online privacy. So how can companies determine whether or not a user is legitimate? The answer lies in understanding proxy services, how they work, and how to detect and block suspicious web traffic.
Types of Proxies

To understand how proxies work, it is necessary to know the differences between the various types of proxy servers. There are data center servers, transparent and forward proxies, and so on. In general, they can be divided into three main categories: Virtual Private Networks (VPNs), web proxies, and Content Delivery Networks (CDNs).
Virtual private network (VPN)
VPNs are commonly used by privacy-conscious individuals and companies who want to encrypt their network traffic. It is a common tool that routes and usually encrypts all network traffic to and through a device. A VPN can be thought of as a secure tunnel where all incoming and outgoing information is protected.
Web proxy
Public proxies or web proxies serve as a gateway between the user and the larger Internet. A web proxy has its IP address that is recognized by your device, and when you send information to the Internet, it is routed through the proxy, which receives a response from the web server and then routes the data back to your browser.
Web proxies come in the form of software and hardware. Cloud service providers usually host software servers. Hardware servers are physical servers located between your network and the Internet.
Content delivery network (CDN)
CDNs are servers distributed across the web space that provide better performance and availability than single servers. They are a widely used tool for legitimate business purposes, e.g., website owners with visitors in different geographic locations can use CDNs to deliver content faster. However, they can also be used to distribute malware.
What Are Traffic Generation Proxies?
Traffic generation proxies are a critical enabler for businesses in the digital age. The primary goal of many companies is to increase the number of visitors to their websites. Search engines are the largest source of organic traffic. A website with high, unlimited traffic is more likely to generate more sales compared to its competitors. Marketers use traffic as a means to increase sales. Real human traffic is essential, but companies also buy machine-generated bots to improve their results.
Although real human traffic is undoubtedly valuable, some companies prefer to generate traffic using tools such as bot traffic generators. Sites that rank high on search engine results pages (SERPs) are more likely to get more clicks, so marketers pay special attention to optimizing their sites to achieve top rankings.
However, a true human web flow is not always enough to have a significant impact on the success of a website. This is where generation proxies come into play. These tools generate unlimited artificial traffic in a bot-generated method. This allows websites to stand out from the crowd and boast impressive visitor statistics, setting them apart from the competition.
What’s more, if you want to increase traffic, you can use search engine optimization (SEO) as an effective and legitimate method. By implementing techniques such as link building and keyword optimization, you can increase the visibility of your site.
How Traffic Generation Proxies Work
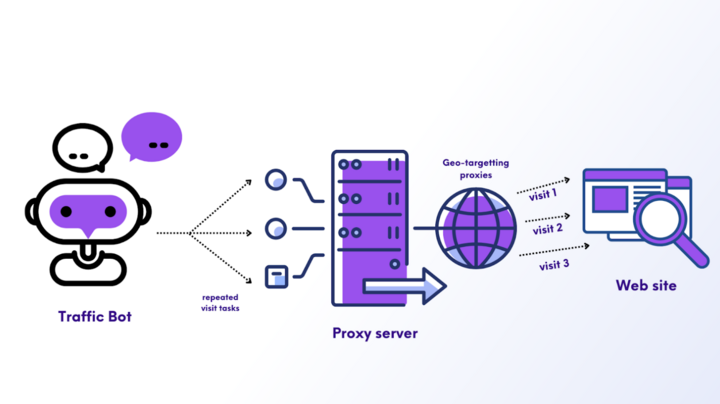
The main purpose of traffic generation is to simulate interaction with a user. A traffic bot is a software that is programmed to update the system and perform a certain set of actions repeatedly. To maintain anonymity on each visit, traffic bots rely on proxy servers. Proxies equipped with pools assign a new IP address each time the bot visits, allowing the bot to repeat the process and give the appearance of real human actions.
Resident proxies are an ideal choice for generation tools. Providers like Proxyscrape offer more than 7 million resident servers, so the proxies in the list can be automatically assigned to each spoofed visit. Since resident proxy IPs are derived from real locations, visitor statistics appear more credible.
Most people think of Internet traffic only in terms of the number of visitors. However, it also includes the number of followers on social networking sites such as LinkedIn, YouTube, Twitter, and Instagram. The followers, views, and likes on these sites create a positive image of a profile in the eyes of the public.
YouTube is a platform where channels try to increase their revenue through views and subscriptions. One effective way to increase subscribers is to make it appear that the channel is already well promoted by generating non-human actions. YouTubers often buy the visibility of actions from bots that generate tasks that look more real.
The Advantages and Disadvantages of Generating Traffic

The benefits of using traffic generation in business
Proxies offer many benefits for marketers to increase conversion rates. Here are some reasons why companies should consider using generation tools.
Easier load testing
Non-human actions also serve the practical purpose of testing your website’s capabilities. Once a site is created, you need to test its resilience by generating large amounts of actions on the server to ensure that it can handle the load without crashing. Load and endurance tests help determine the limits of a server’s capabilities.
Geo-targeting
With the ability to select IP addresses from different locations through geotargeting options, proxy servers can help attract Internet flow from desired locations. For example, some companies want to get more visitors from certain countries to expand their presence in those regions.
Reduces marketing efforts
As a rule, marketers invest a lot of time in increasing the visibility of their websites through SEO and other marketing methods such as social media marketing and brand marketing. Proxies can significantly reduce the workload by automatically generating non-human traffic. With the global access that servers provide, it is easy to achieve a high level of visibility for the website.
Untraceable sources
The purpose of traffic generation is to increase the number of visitors. These fake actions do not come from real users, so it is difficult for web servers to determine their origin. Proxy servers increase anonymity through a chain of pools, so it is difficult for servers to determine the real IP addresses of users.
Boosting SERP rankings
Using traffic generated by bots can improve your website’s search engine rankings. This means that your website is more likely to appear at the top of the results when people search for relevant content, increasing the likelihood of clicks and boosting visibility. Click-through rate (CTR) is an important metric for measuring sales success, and websites that use proxies are more likely to increase sales.
The drawbacks of generation proxies
No tool is perfect, and proxies are no exception. Below is a list of disadvantages associated with using fake visibility.
Inadequate contribution to sales
A higher number of registered visitors can improve a website’s search engine ranking, but doesn’t necessarily lead to an increase in sales rates. Converting visitors into customers remains a challenge for marketers.
Suspicion from web servers or internet service providers
Unrestricted logging into a website can cause ISPs to trace the source of the actions and render the website unusable, which can lead to system failure.
Filtered by secure networks
Advanced security measures, such as Google Analytics, can easily detect and filter out bot-generated tools.
Unethical practices
Marketers may resort to illegal methods to grow their businesses. Using fake visitor statistics to improve a website’s visibility is considered unethical.
How Do Fraudsters Use Proxy Servers?

The main purpose of proxies, malicious or not, is to disguise the user’s identity and location. However, skilled attackers can exploit this technology for more sophisticated scenarios, often with disastrous consequences.
Ad fraudsters use servers with VPNs to redirect the web flow of botnets and click farms through frequently changing IP addresses, making it appear that the clicks are legitimate.
A proxy server can be a valuable tool for scammers looking to exploit higher pay-per-click (PPC) costs in popular regions such as Europe or North America. By disguising their location and identity, they can gain access to these regions and take advantage of click fraud.
The malicious activities range from simple IP address spoofing to using more complicated web servers to mimic the device, network, and other details. A headless browser from Southeast Asia can be used to make a French mobile device with a 5G connection look like a European device.
Even the harmless use of VPNs by legitimate users can cause problems for businesses, however, as it can hinder remarketing strategies and distort marketing data.
Detecting and Blocking Harmful Actions on Your Website

How can marketers identify and prevent undesirable actions? First, they need to determine if the proxy is harmful and should be blocked, or if it’s simply suspicious. When analyzing customer actions, we adhere to a set of best practices to make informed decisions about how to respond to malicious servers. A comprehensive security platform facilitates this process, but it can also be done manually with significant time and effort.
Track the actions
It is extremely important to monitor the domains that visit your website. If you notice an unusual increase in clicks from unusual places, it is a sign that your ad campaigns or website are under attack. If you notice abnormal traffic, check your server logs for suspicious IPs and add addresses to your affiliate or block list.
Analyzing packet headers for suspicious data
Technically savvy users can also check the packet headers for additional information such as the operating system or browser version. If you receive multiple web requests from the same IP address but notice a change in the operating system each time, there’s a good chance it’s proxy, and you can redirect or block it depending on your conditions. To allow proxy users to access your website while keeping malicious users away, you can look out for signs such as the use of Linux or outdated browsers and restrict blocking.
Monitor discrepancies
Take it a step further and identify the cases in which the user makes false claims. If the user appears to be using a mobile device, but the package header indicates the presence of browser extensions, it can be assumed that the user is intentionally providing false information because there are no browser extensions on cell phones.
By collecting all these details, you can assess whether the proxy has malicious goals or it is just a user who wants to protect privacy. Based on this assessment, you can adjust your block list accordingly.
Use complex go-to-market security
If the manual process of detecting and blocking invalid actions seems overwhelming, there is an alternative solution. Using a comprehensive security go-to-market platform can simplify and add value to this process.
Investing in a platform like Cheq Paradome can save time and resources by automatically evaluating website actions in real-time, classifying visitors as invalid, suspicious, or legitimate, and taking the necessary steps to prevent them. Leveraging thousands of security challenges, the platform provides a robust solution to secure your go-to-market efforts and reduce the cost of every action.
Proxy Features in Traffic Generation

Thus, the proxy acts on behalf of other devices to communicate with the target server through its IP address and hide the true identity of the user. Some important features of proxies are explained below.
Anonymity
Using proxy IP addresses, proxies provide users with anonymity when accessing websites. This allows users to access websites from different accounts and impersonate unique users.
Speed
A high-bandwidth internal proxy server can significantly increase the speed of tasks and reduce the time required to complete them. This allows users to visit websites quickly and repeatedly.
Global access
The servers offer geo-targeting options that allow users to select IP addresses from all over the world. This helps you generate web actions from various sources and unblock restricted websites.
No wonder proxy servers are so popular and used for both good and malicious purposes due to these features.
Summary
As mentioned earlier, there are many valid reasons why people use these services, and a large number of users do so every day for both personal and professional purposes.
To keep your website safe and distinguish web traffic, it’s advisable to consider actions from unknown or questionable sources as suspicious, instead of blocking them immediately. Some people hide their identity for harmless reasons, but if their presence on your website makes conversion difficult, you should monitor or possibly block their traffic. It’s worth remembering that even anonymous actions that aren’t malicious can distort campaign data and provide misleading information.
While proxies can provide a quick boost in page actions, they aren’t a sustainable solution for long-term growth. Proxies can help drive traffic to your pages, but they’re no guarantee of real sales. Therefore, marketers should focus on converting visitors into buyers after gaining their attention with a fake web flow.
In conclusion, proxies can significantly increase a website’s visibility and improve sales. If you want to attract more traffic, you should consider using proxy servers in conjunction with the best bots. However, care should be taken to ensure that the bots don’t overwhelm the website with too many actions. Finally, it’s recommended to use fake traffic only for ethical reasons, for example, for research purposes.
Now you know the crucial role of proxies in the world of digital marketing and traffic generation.
