Networking Configuration
What is Network Configuration?

A network configuration is a set of rules that describe the overall network architecture and data flow. These settings are similar to a combination of traffic rules and road infrastructure. Just as it is difficult to move cargo without a road map, it is only possible to process a data packet by setting up a network configuration.
Network configuration determines exactly how nodes within a network communicate with each other. This communication can have a physical or a logical basis.
Physical networks
A traditional setup considers physical connections between devices and settings based on real connections. Installing a physical network is very time consuming. It requires a lot of cable management, configuration and additional hardware to manually set the network configuration.
Logical networks
Today, technologies have evolved. A network structure can be software defined. In a virtual network, the software acts as a hardware device. An administrator can control it remotely, easily change the structure, and use automation tools to monitor and optimize it.
Regardless of the type of network, there are some basic principles for network configuration. What are network settings in general?
- Topology set up
- Priority of nodes
- Configuration of nodes
- Network policies
When setting up a new network, an administrator considers such details as:
- Safety requirements
- Performance requirements
- Possible overloads
- Coherence of the data flow
Physical Networking Configuration
Topology
The establishment of a network begins with the definition of its topology.
A topology is a graphical model that represents a network as nodes connected by links. The nodes are physical/logical devices or clusters within the network. The links are the connections between the nodes. Physical links are real cables and wires. Logical links are virtual channels that show how data gets from one node to another.
There are several typical topologies for building an independent network or local cluster.
Star
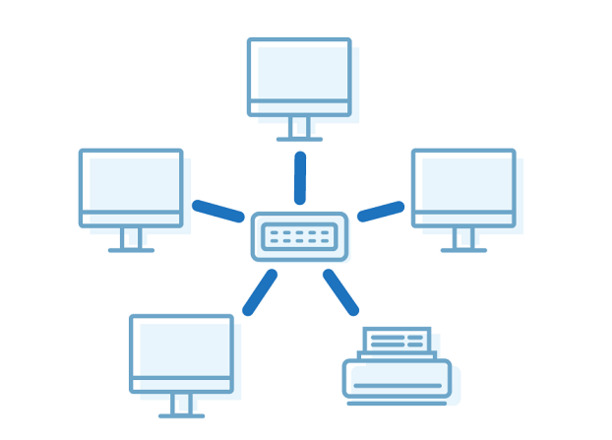
The star is the most popular topology form. The reasons are high performance, safety, and easy maintenance.
In the star topology, all nodes within a network are connected to a single central node. A central node can be a router, a server, or a central computer. It can act as a gateway to inspect and filter incoming data. All nodes are separated from each other and can only be reached via a hub.
Pros
- Scalability. The number of nodes is limited only by the capacity of a central hub.
- Ease of setup. One administrator can manage all connections from the central unit. New installations do not result in the need to reconfigure the entire system.
- Reliability. The star topology is stable because not every device on the network needs to function properly. If one of the nodes fails, the network is not affected.
Cons
- Central node failure risk. Although the stability of the network does not depend on all nodes, it does depend on a central unit. If a central unit fails, all units are shut down.
Tree
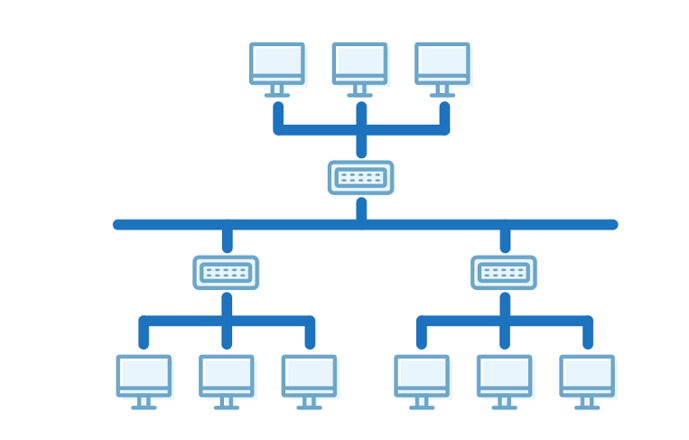
A tree topology has the features of a star topology since a tree represents hierarchically arranged clusters of star networks. A tree topology has a root hub or bus that is connected to secondary hubs that are central to their local star networks. Secondary hubs connect to subordinate hubs and so on, each forming local networks.
Pros
- Scalability. A tree network allows users to easily add new devices and local networks.
- Easy management of heavy structures. Since a tree network can be easily divided into local star networks, each star network can be managed separately. All debugging can be done locally.
Cons
- High risk of a network crash. The whole network depends on the upper hubs. The whole system collapses if a root hub or one of the high-level hubs fails.
- Physically difficult to set up. Each of the devices must be connected in hierarchical order. Sometimes this means miles of extra cable and cable management problems.
Bus
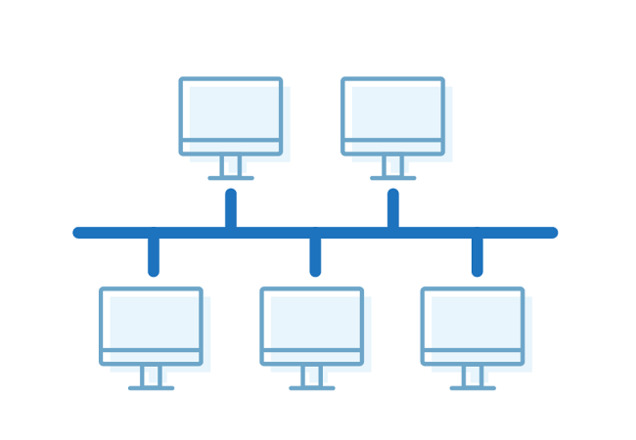
A bus is a type of topology in which all devices in the network are connected to a cable or logical channel. In this type of topology, nodes are directly connected via a bus. This is a good solution for temporary networks or when new devices need to be added quickly.
Pros
- Easy installation and management
Cons
- Overload possibility. In this network topology, data streams are not distributed. With high traffic volumes, there is a high risk of collapses or delays.
- Low security. There is neither a hub nor an internal device to check incoming data.
Ring
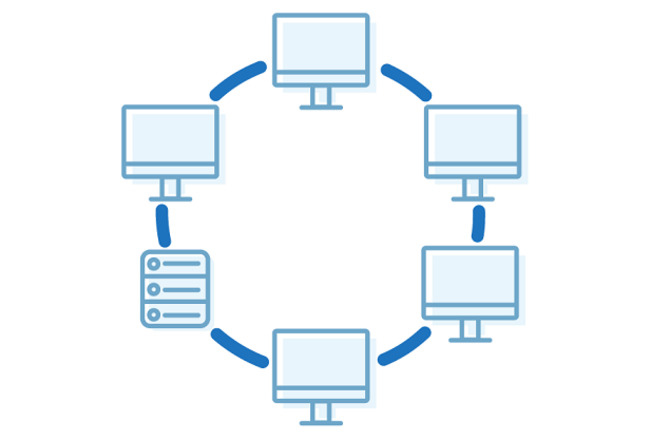
A ring topology is an extended bus topology. All devices are connected to a cable one after the other and form a circuit. A ring topology uses token ring technology for data transmission. A token is a piece of data that circulates through a network. Only a token holder can send the data to avoid data collisions within a communication line.
Pros
- No collisions. Even though token ring technology is now obsolete, years ago a ring was the most effective way to avoid data collisions.
Cons
- Poor scalability. It is hard to add new nodes to the ring.
- High risk of collapse. Even when one of the devices goes down, the whole network fails.
Mesh
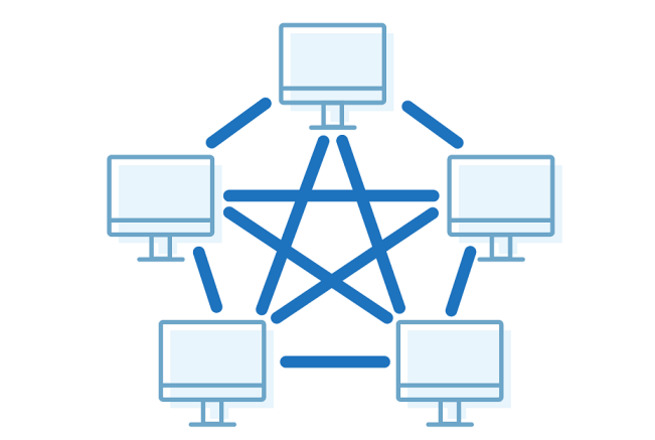
Mesh is the most developed type of interconnection. In a mesh topology, each node is connected to all others. Nodes can send information to all other nodes simultaneously (flood) or use a direct path.
Pros
- High security. Each pair of devices has a point-to-point connection to prevent unauthorized access.
- Robustness. The mesh is probably the most robust topology type. Any node in this network can fail without damaging the entire system.
Cons
- Time-consuming physical installation
- Difficult system management
Configuration of Network Devices
After a network topology is created, the second step is to set it up. An administrator first defines central nodes, if any, and then secondary nodes.
Most networks use a switch or router as the central unit or hub. Configuring a switch or router is critical to the proper functioning of the network.
How to configure a network switch
Network settings depend heavily on the hardware, firmware, and software used. The variety of network hardware is huge. Switch hardware can differ by access options, user interface, supported network parameters, etc. However, there are some basic stages that the administrator should consider when configuring a switch manually:
- Connect the switch directly with a cable or remotely through an administrator’s computer.
- Install the configuration software (Hyper Terminal, PuTTY) on the administrator’s computer PC, if remote access is available.
- Set up the management IP address.
- Set up a hostname.
- Enable the password for the switch.
- Add a domain name.
- Check the existing VLAN networks. All switches typically have at least one default network configuration.
- Create new VLANs. Each new VLAN usually relates to a specific local network, such as the engineering department or the marketing department.
- Assign each new VLAN to a physical port.
- Assign IP addresses to the VLANs.
- Assign appropriate IP addresses to the devices on the network
How to configure a router
Like switches and other networking hardware, routers have different user interfaces and parameters depending on the model. Some models allow more configuration settings than others. The basic phases that an administrator should always remember are:
- Connecting a router to a PC
- Access the router’s user interface. Almost all routers can use a web interface for setup.
- Create an admin login and password for network management
- Assign a network SSID if you are configuring a wireless network
- Set up an internal IP address range
- Set up port forwarding
- Configure additional settings such as DHCP, WPS, dynamic DNS, etc.
Getting a report
After the basic setup of a physical network is complete, an administrator can check the work of the system.
How to check the network configuration
To check the network configuration, open the Windows command line and use the following commands:
ipconfig – displays the current TCP/IP network configurations in the Windows environment.
ipconfig/all – displays all network interfaces.
For Linux terminals use these commands:
ifconfig – displays network configurations in Linux environments.
ifconfig -a displays all network interfaces.
How to print a network configuration page
When the network is ready, the administrator must generate a report. A local printer can do this in seconds. A local configuration page contains not only the printer’s IP address but also valuable information about a local network.
Different printers offer different methods to print the network configuration page, e.g:
- Press the Information(i) button to print the report immediately. (Canon PIXMA HOME TS3160, Canon G3411).
- Press and hold the Wi-Fi button until the green light flashes, and press the Wi-Fi button again. (Canon PIXMA HOME TS6060)
- Press and hold the Print button. (HP LaserJet P2015)
- Use the printer menu and locate LAN Settings – Print (Canon PRO -1000, Canon OFFICE MAXIFY)
Installation F.A.Q.
What do computer system and network configuration mean? Why is it important?
Proper network configuration ensures data security and system stability. It has a great impact on the characteristics of data traffic and fast data access.
What level of system and network configuration does an organization network need?
Organizations usually have three levels of security:
Minimal protection secures a small local network from the most common threats. Small businesses use antivirus software, firewall protection, and regular vulnerability assessment.
Moderate measures to protect midmarket companies from untargeted attacks. These companies use additional security components:
- Network segmentation
- Email security
- Intrusion detection systems
Maximal protection is common for large companies. Maximum protection includes various additional methods and technologies to protect the data, for example:
- Cloud network environments
- Encryption of data traffic
- IAAS networks with integrated security services
What does an error configuring network mean?
Some devices experience errors when connecting to the network. The error message “Configuring network” usually appears when you try to connect to a wireless network. To connect a laptop after an error occurs, forget about the network and add it to the device again.
Logical Networking Configuration
Modern network configuration is much more complex than configuring a local network with a switch or router. Large distributed networks require a completely different type of management based on load balancing and data distribution.
Token Ring technology was invented in the 1980s to avoid congestion and data collisions. Nowadays, there are more complicated ways to load balance. Data can go through a proxy to lighten the load on the servers and keep the data safe. There are two common ways to use a proxy as a hub: Edge proxy and Sidecar proxy.
Topology
Edge Proxy
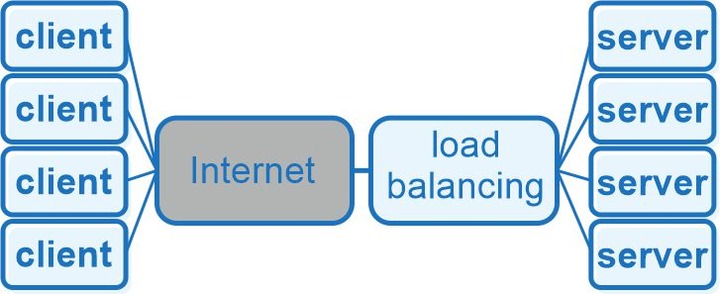
In the Edge (Middle) topology type, a proxy server is an entrance hub for the data to access backend services.
Sidecar Proxy
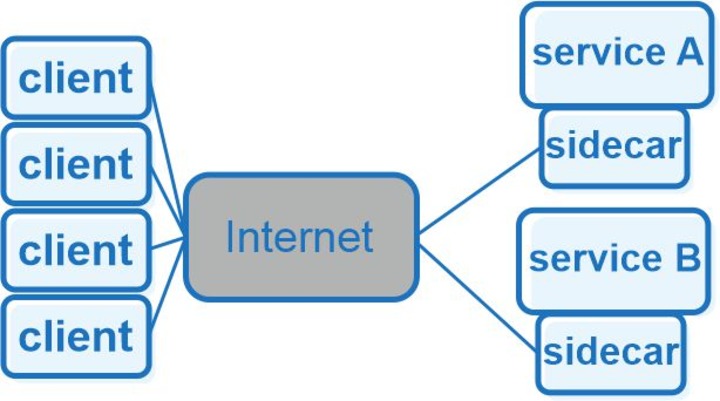
Sidecars are typically deployed within a service mesh architecture. They control internal network communication and are embedded as part of microservices. An example of a service mesh infrastructure is Istio + Envoy
Service Mesh Architecture: Istio+Envoy
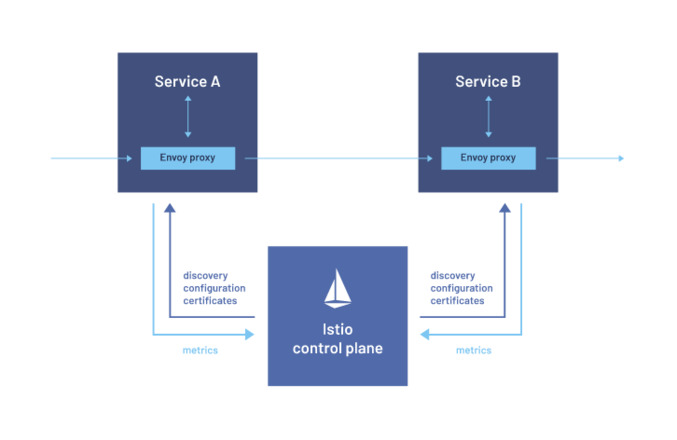
A service mesh architecture consists of the following:
- the Data Plane: Two microservices with embedded side-car proxies.
- the Control Plane: services for network management, configuration, and certificates.
Istio Definition
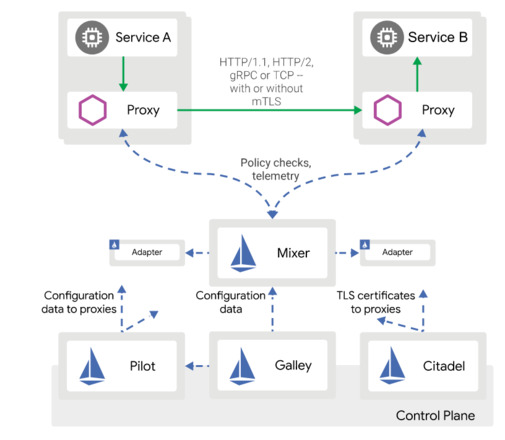
Istio is a service that overlays the existing network infrastructure to manage traffic, configure networks, and create routing rules.
The Istio data plane includes microservices with embedded Envoy sidecar proxies. Istio Control plane consists of the tools and dashboards to configure the network, such as:
- Istio Pilot for traffic management and configuration of proxies
- Istio Auth for authentication control
- Istio Mixer for monitoring
- Istio Galley for validation of changes
- Istio Citadel acts as an internal CA for issuing certificates.
Istio also has several add-ons for network monitoring, creating records, and retrieving metrics: Prometheus, Grafana, Kiali, etc.
Envoy Definition
Envoy is an open-source microservices-oriented proxy. It can be used as a middle, edge, or service proxy and also as a data plane within a microservices architecture
Envoy supports the most important functions for a data plane proxy:
- Load balancing
- Health check
- TLS termination
- HTTP/2 and gRPC support
- Circuit breaker
- Statistics for network systems
- Telemetry data for system monitoring
Istio + Envoy helps with load balancing, traffic flow control, and traffic route management.
Istio and Envoy Configuration Example
The main steps to configure Istio with Envoy Injected are:
- Download the Istio core
- Install and configure Istioctl
- Deploy a microservice application
- Inject Envoy into the microservice pods
- Install Istio visualization addons
Examples of Envoy Proxy configuration can be found on the official Envoy Proxy page.
Conclusion
Setting up a network configuration means doing a lot of research and finding optimal data access and transfer solutions. Whether it’s a local physical system or a complex cloud-based solution, network configuration solves the problems of speed, performance, security, and overall network effectiveness.
