How To Protect Yourself From Cybercrime in 2025?
Most people try to protect themselves on the Internet by assigning strong passwords to their accounts. They do not open suspicious emails, use a top-notch antivirus program, and sometimes check the user’s consent file. But is that enough to protect against cybercrime?
To avoid the risk of a cyber breach, you must first understand the definition of cybercrime and its various forms. Yes, it’s not just about stealing credit card data or infecting your computer with malware.
In this guide, we cover the different types of cybercrime and all the precautions everyone should take to stay safe when browsing the Internet.
What is Cybercrime?
In short, cybercrime is any crime directed against an online user or group of users. It can range from a simple scam email to a serious organized crime involving IT specialists.
In addition, cybercrime is the term used to describe various crimes committed with the help of the Internet – for example, kidnapping followed by e-mail blackmail.
According to Forbes, the mid-2022 cyber statistics in the USA were considered alarming due to the significant increase over previous years.
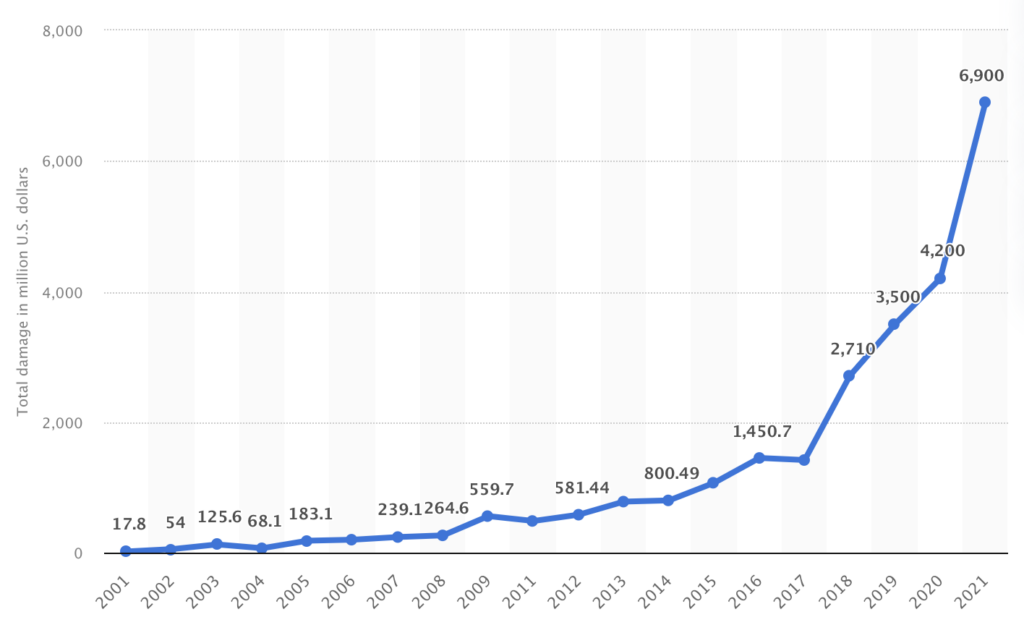
The problem is that modern technologies are constantly evolving, so cybercrime is also becoming more sophisticated. The good news is that most crimes are still based on users’ lack of knowledge. So after reading this article you will be at least 50% better protected!
What are the Types of Cybercrime?
What exactly can happen to you when you are on the internet? What dangers can a company face with its websites or private data? The number of dangers you can face online is immense, so we’ll focus on the most prevalent types of cybercrime in 2025.
Cybercrimes Aimed at Individuals
When criminals prepare for a massive or targeted cyber attack, they usually pursue one (or both) of two goals: To steal money or personal information. Here’s what they can do.
Identity Theft
A very common form of cybercrime is the theft of personal information that you disclose on the Internet. This information can range from your credit card number to the contents of your passport or your Social Security number.
After gaining access to personal information, intruders can use it for a variety of purposes. For example, they can make purchases with a stolen credit card to resell the products later. Even more troubling is the theft of a Social Security number (SSN), a personal tax number that can be used to prove a person’s identification in the United States.
Because many modern financial institutions can accept credit applications electronically, a criminal can use the SSN to apply for credit in the name of the holder.
Identity theft is often the result of a security breach in an organization that stores large volumes of user data. A recent example is the U.S. mobile communications company T-Mobile, where a major hacker attack led to the loss of more than 70 million records.
Social Engineering
This type of cybercrime does not always require advanced means of infiltrating software. Human relationships are the basis of social engineering. Sometimes their goal is to gain the user’s trust so that he or she will voluntarily provide all the necessary data.
The $40 million Ubiquiti Networks breach is a well-known example of social engineering cybercrime. The fraudsters did not compromise any systems but sent an email on behalf of the company’s management asking the finance department to pay the attached invoice.
The well-known fraudulent dating stories, where a woman pretends to be in a relationship to ask her boyfriend for money online, are also nothing more than social engineering. In general, there are several ways to deceive people criminally, and the following are the most typical ones.
- Phishing. The goal of phishing is identity theft, and the traditional method is to send emails with malicious links. The criminals disguise these emails as messages from a well-known company and ask recipients to click on a link and register. For example, it might be a fake email from your bank informing you about a data breach and asking you to change your password or provide personal and credit card information.
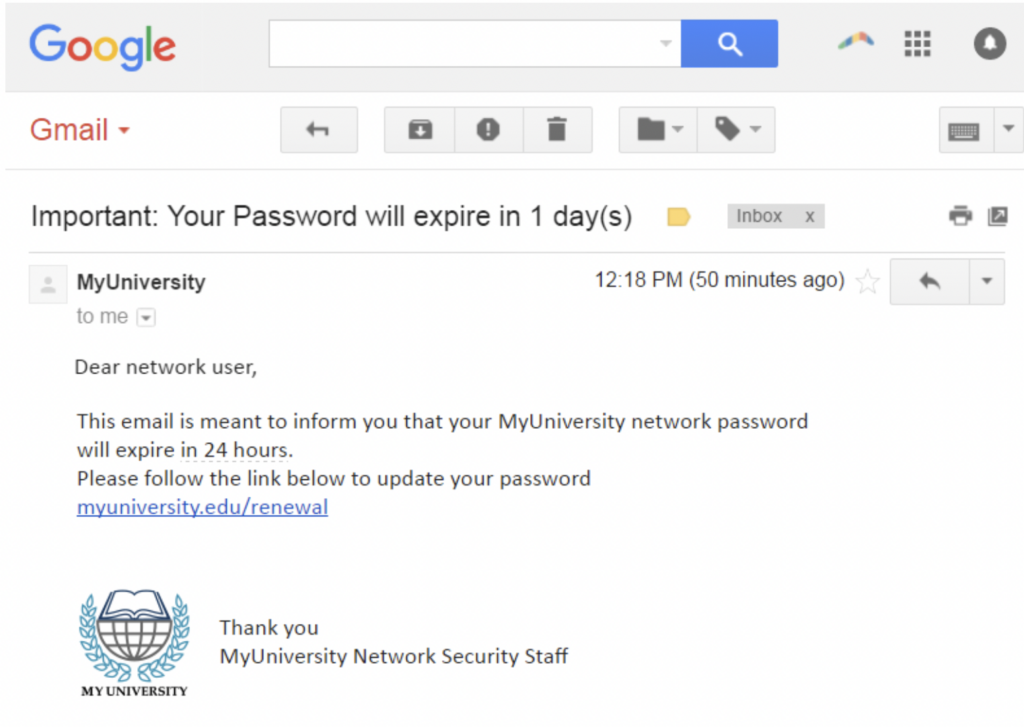
Another variant is the Trojan: in this case, a malicious link leads to a virus that steals personal data from your PC.
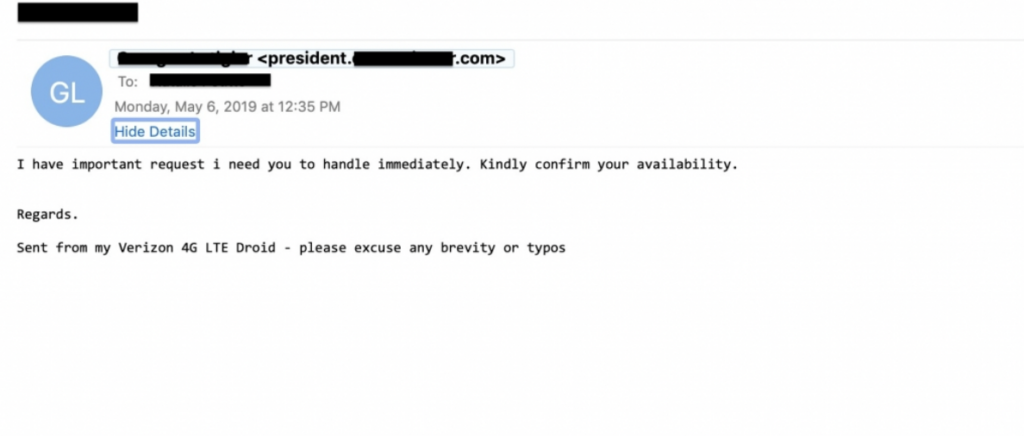
- Pretexting. An intruder poses as a tech support representative and offers to solve software problems. In reality, there is no problem with the program. A deceived victim, on the other hand, trusts an invader and directly gives him important data needed “to fix system problems’ or simply grants him remote access to his PC.
This cybercrime situation can vary. For example, a thief may pose as a bank manager or even a family member. Fraudulent call centers use stolen phone numbers to contact hundreds of potential victims every day.
IoT Devices
The enormous popularity of Internet of Things (IoT) gadgets – anything labeled “smart,” such as watches or kettles — has a downside. These devices are extremely vulnerable to cybercrime because they are constantly connected to the Internet and lack adequate security. Smart devices cannot be appropriately protected due to their limited memory, capacity, and storage space.
So what can potentially happen? An intruder can hack your device and gain access to the network to which your refrigerator or smart speaker is connected. The rest is paperwork: after the hack, accessing your device and sensitive data becomes all too easy.
Cyberstalking
Stealing money or data is not usually the goal of cyberbullying. It can sometimes seem more or less harmful. For example, if you frequently receive nasty comments on your Instagram posts from the same person, you should consider this as cyberbullying.
However, this subset of cybercrime also includes more serious forms of abuse. For example, some cyberstalkers may hack your camera and use the images to blackmail you. In addition, stalking can also involve the following:
- tagging the victim in certain social media posts,
- regularly sending threats, sexually abusive content, or weird love confessions of love,
- disclosing personal information about the victim on the Internet
In one of the examples of cyberstalking cases in the USA, a woman complained about a user who had been sending her text messages for three years. He harassed and intimidated her and asked her to send him nude pictures.
Potentially Unwanted Programs (PUPS)
If you use an antivirus program, you have probably seen this message a few times:
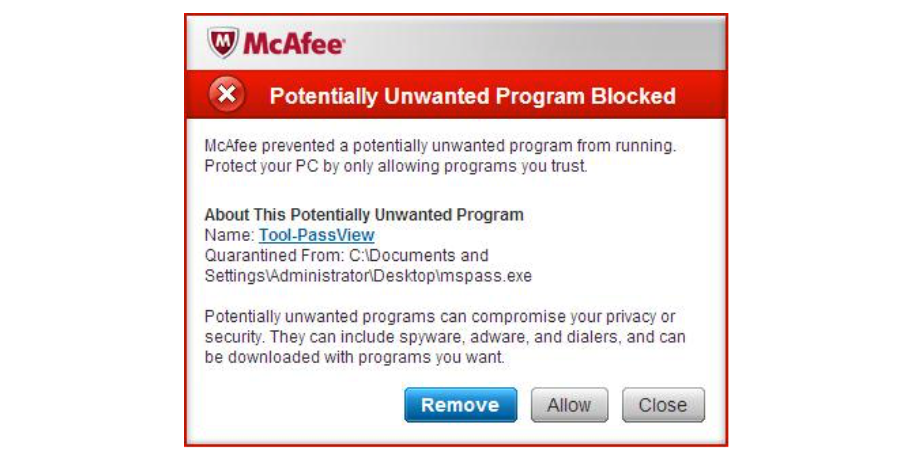
What does it imply? Is it a red alert and a possible virus download? Not always. A PUP is not malware. It may look like normal software, but it contains important bugs that you should be aware of.
Some of them are not harmful, but they can ruin your experience:
- slow down browsers or the operating system
- start showing you advertisements you never requested
- add browser toolbars you don’t need and realize they consume a lot of memory
Instead, they may store and use this information to send you targeted or, on the contrary, to manipulate your opinion through sponsored advertising. Even though this is not the most serious Internet crime, your privacy is still violated, which is why PUPs cannot be considered completely safe.
Cybercrimes Aimed at Businesses
All of the forms of cybercrime described above can occur in organizations. Corporate employees may receive phishing emails or download malicious software. However, some hostile operations are specifically targeted at companies or affect corporate websites.
DDoS Attacks
A distributed denial of service (DDoS) attack targets a network or server and cripples it. Technically, it works as follows: A server receives a large volume of spam traffic, hindering legitimate traffic.
As a result, visitors are unable to access the attacked website or it starts responding slowly. Such a cyber-attack can be carried out by a competitor or used to blackmail a website owner.
Brand Exploitation
Individuals are most affected by cybercrime. However, corporate websites are also attacked, resulting in significant reputational damage to organizations.
Brand exploitation, often known as web jacking, involves tricking people by imitating well-known websites. Sometimes the target is phishing; for example, a full clone of an online store may intercept credit card information or passwords.
In some brand exploitation methods, users are charged for services or goods believing that they are ordering from a legitimate website.
How to Protect Yourself From Cybercrime?
Both individuals and businesses need to be educated on how to protect themselves from various types of cyber threats. A personal PC, IoT device, or smartphone, but also corporate clouds, servers, or employee laptops can become a target. So what are the ground rules for survival?
Let’s start with general tips for casual users.
- Make your password check-up. Do you use the same password for all your social networks, bank accounts, and forums? Unfortunately, now is the time to change it. Also, make sure your passwords are long enough (at least 10 characters) and consist of letters, numbers, and special characters.
- Install a proxy. A proxy acts as an intermediary between a person and the website they visit. In this way, it hides the user’s actual location, provides anonymity on the Internet, and offers additional security.
- Don’t click any random links. Even if you have received an email from your best friend, you should not open links or download anything.
- Use only official websites. If you come across a copycat of your favorite marketplace, your online shopping experience could be disastrous. Check if the website is genuine by comparing the domain with the original version on Google.
- Protect your network. A secure password is also important for the WLAN, and not because your neighbors can use it secretly but to protect yourself. Share your password only with people you can trust.
- Use an antivirus. Even if you are pretty sure that you will never come into contact with malware, an antivirus program is a must. Who knows the new and non-obvious methods that intruders might use?
- Be careful with public networks. If you are connected to free Wi-Fi, it is not the best idea to work with sensitive data on your smartphone or laptop.
How to effectively prevent cyber-attacks in organizations?
Enterprise security and cybercrime protection are more complicated. Not only do they need to protect individual employees, but they also need to invest heavily in the security of services and internal networks. Companies spend an average of 10% of their annual budget on implementing and maintaining specialized security software.
So what does this investment include?
Step 1: Incorporate Zero Trust Inspection
Simply put, the zero-trust model is a security principle in which every login request and user must be considered a potential threat. The model requires constant monitoring and review of credentials – for every user, every location, and every device.
The guidelines for Zero Trusts include the following:
- VPN use for all employees
- Implementation of firewalls for servers
- Control of all IoT devices
- Automation of monitoring processes for timely alerts on security breaches
Sometimes a company, especially a small corporation, may lack the means to ensure a high degree of protection. Outsourcing is useful in this situation, where a managed service provider can handle all or part of the cybersecurity tasks.
Step 2: Create Save Data Sharing Practices
Corporate emails and messengers are highly vulnerable to cyberattacks. For this reason, companies tend to implement modern solutions than simple files attached to Slack or Gmail. Here are some of them:
- special software for employees to share files within a company
- cloud services such as DropBox or in-house corporate clouds
- encryption software that protects files from being opened without an individual key
Step 3: Perform Regular Cybersecurity Checks
To protect against DDoS attacks or to quickly find and fix security vulnerabilities, it’s important to constantly keep an eye on upcoming traffic. What are the signs that something is going wrong?
- The network is slowing down. All of your websites are performing poorly.
- Your websites are unreachable.
- Your websites are experiencing a sharp increase in traffic for no apparent reason.
Step 4: Install Antiviruses
All work PCs, including those of contractors, must be equipped with paid antivirus software. If your company stores a lot of susceptible data, a corporate firewall is a good idea.
Step 6: Use CDNs
The content delivery network is abbreviated as CDN. In short, it’s an alternative to a regular server that allows consumers to load web pages faster.
Apart from this significant advantage, CDNs also improve website security. For example, it was one of the first tactics used to fight DDoS attacks.
Step 5: Teach Your Employees
Humans are the most vulnerable part of the entire cybersecurity system. Even if your anti-DDoS measures are working perfectly, any person in your office, including contractors, can become a victim of cybercrime. So make sure all employees are familiar with the company’s security policies.
These guidelines could also include the checklist for individual cyber protection that we showed you above.
How to Report Cybercrime?
Suppose all precautions and methods to prevent cyberattacks fail. A cybercriminal has victimized you or someone you know – what to do?
Of course, you should file a cybercrime report, but how do you do that? Depending on the jurisdiction, different bodies may be helpful:
- USA: you can either contact the Internet Crime Complaint Center or submit an online complaint to the FBI, which will forward your request to the responsible body.
- Europe: visit the Europol website, select your country, and follow the instructions for reporting cybercrime.
- India: call the National Cyber Crime Hotline in 1930.
- China: File the complaint at http://www.12321.cn or call 12321.
Key Takeaways
In summary, while cyber attacks are becoming more professional, protection methods are also advancing. Even the basic rules of cyber security help to avoid many unpleasant mishaps. Businesses need a more professional and complex approach that includes various technologies and employee training.
